Understanding Face Verification Threats
Presentation attacks are hitting harder
Fake photos, screen replays, masks, and 3D prints are everyday threats for digital companies. This piece outlines the most common attack types and shows how modern safeguards stop them.
Explore the guide

Deepfakes areon the rise
As deepfake tools become more accessible, fraudsters are using synthetic video and images to bypass IDV. The article breaks down what deepfakes are, how they’re exploited, and how businesses can fight back.
Learn how to spot deepfakesImpersonation attacks are growing
AI-driven fraud has gone mainstream, with deepfakes, biometric fraud, and identity spoofing now among the top threats to digital onboarding. The blog post shares key findings from Regula’s 2025 global survey, revealing how businesses across industries are experiencing and responding to these attacks.
Read the survey insights
How Face Verification Works:Exploring the Basics
What to Look For:Must-Have Technologies
Face matching
Even when a presented ID document is legitimate, KYC systems still need to be sure if the document’s owner is indeed the person being verified. That question is answered through face matching.
Learn more about face matching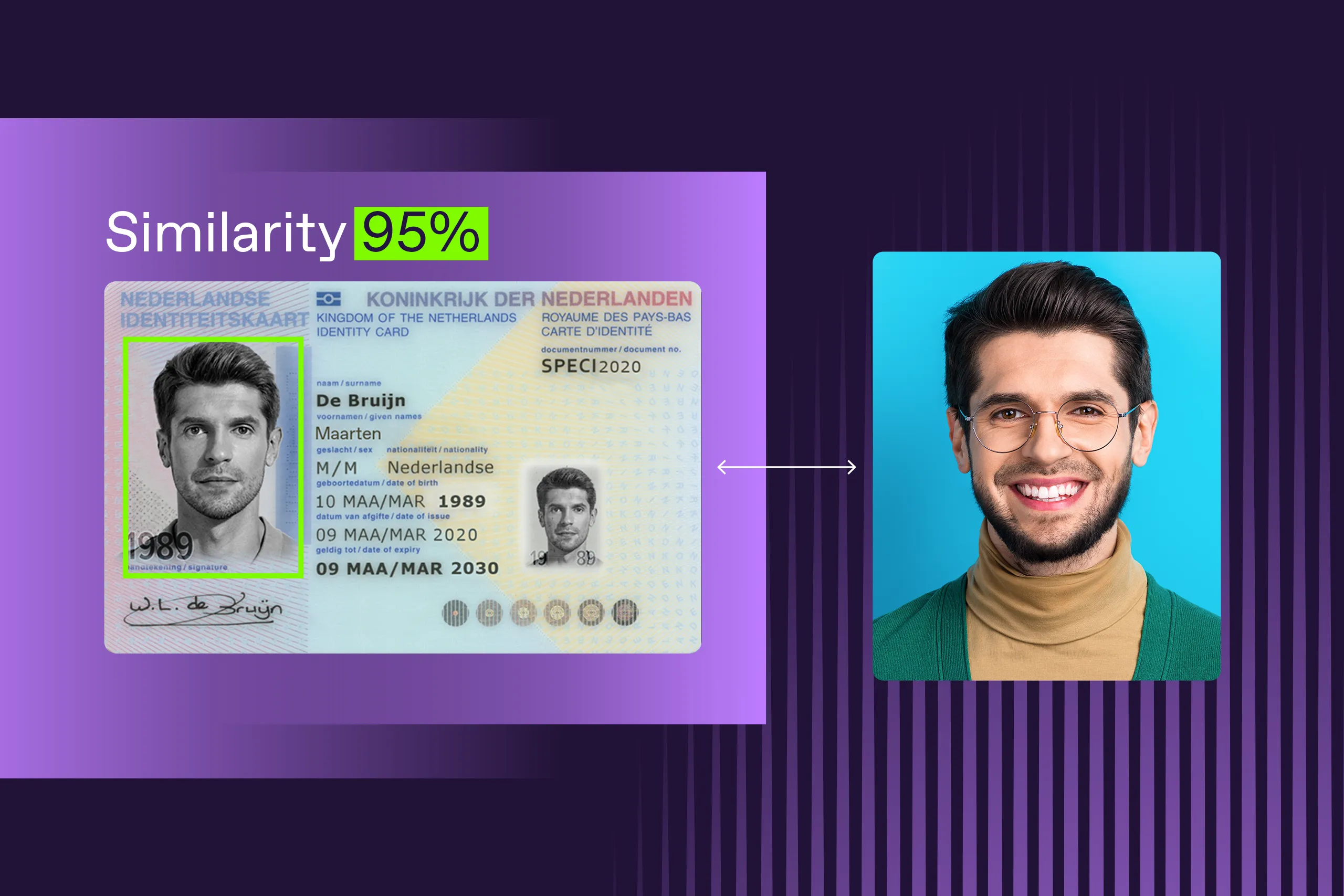

Liveness detection
Fraudsters are getting craftier—spoofing, replay attacks, masks, video manipulation, injections—so relying on a single check isn’t enough. The article explains how to detect such attacks while keeping the UX seamless.
Read the guideDeepfake detection
Synthetic video and images are increasingly used to bypass ID checks. This piece shows how deepfakes exploit weak points in verification flows, and provides strategies to detect and block them.
Explore deepfake defense strategies

Video injection attack detection
Fraudsters can bypass real-time capture by injecting fake video streams directly into the verification pipeline. The blog post shows how such attacks work, why apps are vulnerable, and how to protect your process with feed-integrity checks.
Learn how to detect video injectionsVideo identification
Remote onboarding via live video remains popular across industries. This article breaks down how video ID verification works, where it adds value, and how to deploy it effectively.
Learn more about video identification

Global legal framework is changing
As AI-generated media becomes more convincing, governments worldwide are racing to regulate its use. The article examines the latest laws, their impact on IDV, and what organizations must do to stay compliant.
See key 2025 updatesCommon Use Cases in Face Verification
Bonus: Biometric Verification Assessment
After deploying a face verification system—even in a trial period—it’s critical to evaluate its performance. But measuring accuracy and reliability is easier said than done. These guides provide practical advice: Identity Verification Metrics: How They’re Calculated and Why They Often Mislead How to Evaluate the Performance of Your Biometric System Are Businesses Overtrusting Biometric IDV? An Expert Opinion
Confirm Identity with Regula SDK
Fight presentation attacks with a customizable system for face recognition, matching, and liveness detection.
See all features