What to expect in this blog
Digital companies from regulated industries often need to identify and manage users across a mix of identity and access management tools. As the number of customers or employees grows, this process becomes increasingly complex — and less secure. This article explains what identity orchestration is and how it helps simplify identity lifecycle management through automation and prebuilt settings.
Regula’s global survey found that 43% of identity verification (IDV) professionals face challenges when trying to automate and orchestrate IDV processes across sectors like aviation, crypto, banking, and fintech.
Similarly, 44% say that automated orchestration of IDV tools and workflows is essential for effectively managing diverse user scenarios.
These insights underscore the growing role of digital identity orchestration as a strategic approach in IDV.
In this article, we’ll walk you through what identity orchestration means, how it works, what the major benefits are, and where it fits into today’s IDV landscape.
Subscribe to receive a bi-weekly blog digest from Regula
What is identity orchestration?
Imagine a new client signing up for a mobile app. Once they’ve confirmed their identity through document and biometric checks, they become a new user in your system.
From that point on, the user’s digital identity is now represented in your systems through verified attributes, credentials, and ongoing activity. Their in-app actions — from logging in to changing a password — can be tracked and audited. The personal data they submitted during verification must be securely stored and regularly updated. If they perform suspicious activities like transferring large sums, logging in from restricted jurisdictions, or frequently resetting passwords, it may trigger additional checks or manual reviews.
Elements like access control, authentication, and policy enforcement are typically handled by identity and access management (IAM) systems. IDV tools support these decisions by providing verified identity data and risk signals, but they don’t enforce access themselves.
The challenge is that these systems can be diverse and scattered across a company’s infrastructure. Some are on-premises, others run in different clouds, and they’re often integrated with multiple identity service providers and legacy tools.
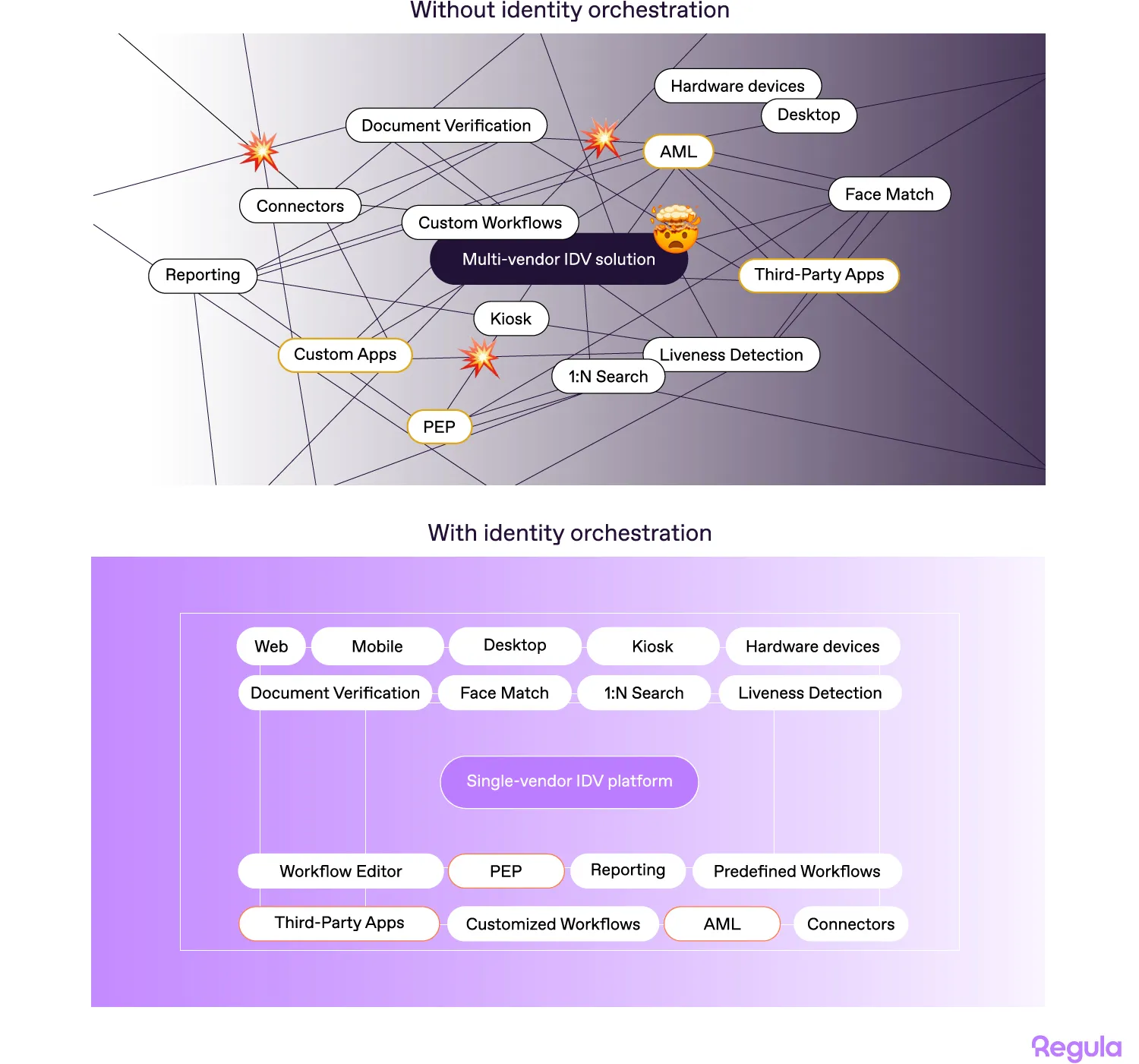
Digital identity orchestration is designed to address this complexity. It acts as a control layer that coordinates identity signals, verification steps, and decision logic across distributed systems.
What IDV tasks does identity orchestration solve?
To better understand a concept like digital identity orchestration, it helps to view it through real-world examples, such as user activities or specific business needs.
Here’s what digital identity orchestration software enables companies to do:
1. Automate IDV processes
Every online transaction a user makes contributes to their digital identity lifecycle. It often starts with basic actions like signing up, verifying documents, and taking a selfie. In regulated industries like banking, these actions are typically part of multi-step processes such as opening accounts, transferring funds, or applying for loans.
On the administrative side, identity-related tasks include logging and auditing identity checks, scoring risks during onboarding, and setting restrictions for specific transactions across various systems and apps.
With orchestration in place, IDV processes follow shared decision logic that defines which checks are required, in what order, and under what conditions. This lets organizations apply document and biometric verification selectively, escalate to manual review when needed, and reuse past verification results across systems.
2. Ensure consistent identity management
Once a user is onboarded, they should follow certain IDV rules set for the system, no matter where they are. But the more users interact with a company’s services, the harder it becomes to keep identity management both secure and consistent.
In practice, this means keeping user profiles up to date: personal details, compliance requirements, and allowed operations must all be maintained.
For instance, a government-issued ID used during registration may have expired, so the user will have to provide a new one. Or, a user may try to transfer funds to a flagged account: in this case, a selfie verification can confirm it’s not a case of fraud or account takeover.
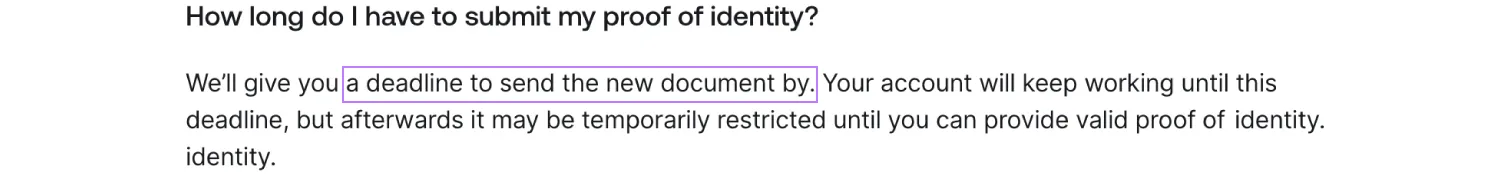
Digital banks like Revolut set deadlines for users to update their IDs. With many users on board, it makes sense to automate this process — and orchestration streamlines it.
Sometimes updates apply not to a single user, but an entire customer group. Imagine a new regulation requiring age verification checks is introduced in a specific country: you must then activate that rule everywhere across your system.
Digital identity orchestration tools help apply IDV policies consistently and automatically across platforms, whether it’s a small system or an enterprise-grade one. What’s more, all regional regulations can be configured to keep these processes compliant.
3. Improve security and user experience
Distributed systems spread across third-party clouds, company servers, and legacy tools often come with security gaps, inconsistent workflows, and more room for human error. Manual management only makes it worse.
This setup also complicates fine-tuning user flows. For example, your policy might require stricter checks for users from certain regions. But those users can have different risk levels. One customer may trigger enhanced due diligence checks because they’re a politically exposed person (PEP), while another may pose a higher fraud risk due to their location.
In fragmented environments, limited visibility and rigid decision logic can result in very different risk profiles being treated the same way, causing unnecessary delays, extra manual reviews, and user frustration. For instance, a low-risk user might be escalated to a video call due to overly broad rules.
Digital identity orchestration software helps solve this by letting you build custom, automated workflows tailored to specific scenarios and designed to work across platforms. With clearer rules and better context, organizations can apply security measures that match the risk level without sacrificing the user experience.
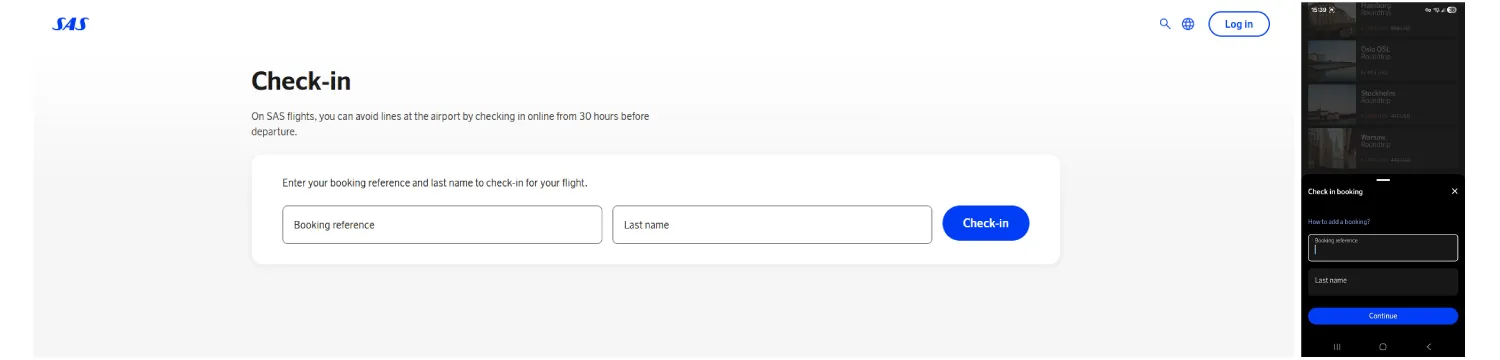
SAS passengers can check in remotely via website or mobile app, which is a common practice among airlines. Digital orchestration ensures rules apply consistently across channels.
Additionally, when identity orchestration is handled by a single vendor like Regula, all sensitive data and account logs are usually stored on-premises, e.g., on a company’s servers or a private cloud. That adds an extra layer of security.
4. Support compliance with identity-related regulations
Identity management must comply with a growing list of global and local laws, from GDPR and CCPA to industry-specific KYC and AML regulations. These rules vary widely by region in terms of what data can be collected, how it’s stored, and where it can be sent.
For example, in the UAE, financial institutions must not only verify ID at onboarding, but also perform additional checks based on transaction value, customer type, and risk indicators. What’s more, the IDV flow may differ for citizens and international residents, the latter of whom may be required to undergo on-site checks. Keeping all customer data on-premises is another key requirement.
Compliance also includes ongoing monitoring, audit trails, and regulatory reporting. In Türkiye, for instance, crypto providers must track and report suspicious transactions to MASAK, the Financial Crimes Investigation Board responsible for preventing money laundering and terrorism financing across all sectors in the country. The information-sharing rule also includes access to records, documents, and, if required, passwords and keys when requested by the regulator.
A digital identity orchestration solution supports compliance by allowing organizations to define verification rules at the workflow level, such as which checks to run, how to handle personal data, and how long to store it based on country, user type, or risk level. This centralized setup also streamlines monitoring and reporting, as all IDV events and outcomes are logged consistently and can be accessed through a single interface, turning compliance from a fragmented task into a structured, auditable process.
How identity orchestration works
Now, let’s take a closer look under the hood.
An identity orchestration setup doesn’t replace IAM systems. Instead, it sits between them, coordinating how different identity tools are used across verification workflows.
To understand how this works in practice, it helps to break orchestration down into its core building blocks.
Identity verification components
These are the tools involved in IDV workflows, such as document verification, biometric checks, fraud screening, and compliance controls. On their own, they perform individual checks; orchestration defines how and when they’re combined within a broader identity process.
Take customer onboarding, for example. In remote IDV scenarios — especially in regulated or high-risk industries — this process typically includes at least two steps: document authentication and a biometric check. In practice, these are just parts of a broader workflow that begins when a user signs up. Even a simple IDV process may rely on more than one tool, such as one for document checks and another for biometric verification.

The IDV process is unique to each company. A complete IDV flow powered by Regula includes these steps.
Additional components often go beyond basic document and selfie verification. They may include sanctions and PEP screening as part of KYC processes, AML-related controls, liveness detection, and reporting. All of these components need to be integrated across multiple entry points, from hardware passport readers and self-service kiosks to third-party applications and web platforms.
Identity workflows
Identity workflows map the paths users take through different IDV components, such as document and biometric verification systems, access controls, notifications, manual steps, and external data sources such as government databases and watchlists. These workflows are complex and often tailored to each customer.
From an organization’s perspective, identity workflows reflect real-world business scenarios, incorporating all required verification steps and decision logic. In a single case, a user might complete a basic document check, move on to biometric verification, or be flagged for manual review, depending on context, risk level, and regulatory requirements.
User profiles and sessions
Each customer interacts with the system through a defined business workflow. Typically, they can manage their account and perform specific actions like making payments, requesting services, or upgrading their plan.
Many of these operations are supported, secured, and tracked by IDV components. For instance, before transferring funds, the system needs to confirm that the action is legal and appropriate for that specific user, based on their region or status.
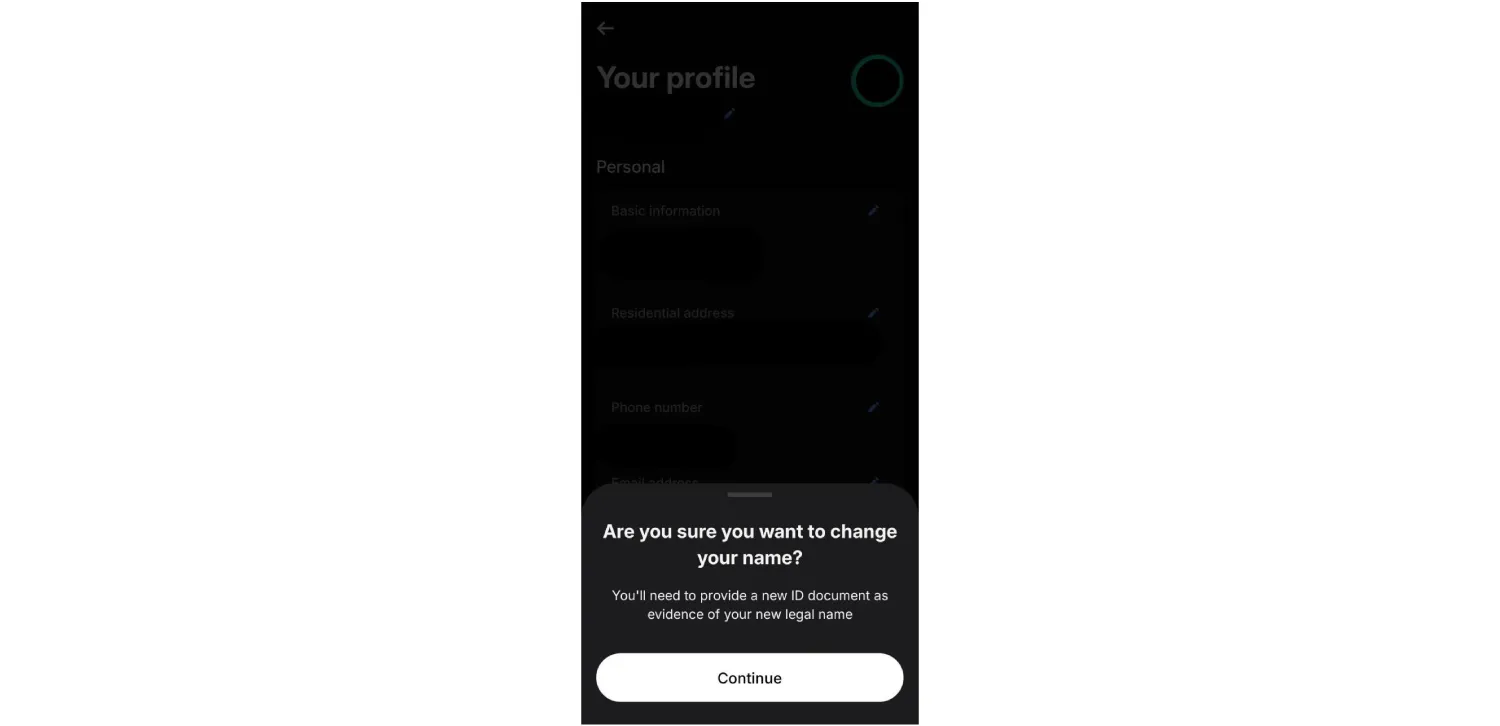
IDV processes are often built into everyday account actions. For example, when a Revolut user changes their personal details, the system prompts them to confirm the change with an updated ID.
Each identity-related interaction between a user and the system creates a session which can be logged for ongoing monitoring. These sessions follow the rules of a given workflow and end with a clear outcome: success, failure, abandonment, or termination. Over time, they give full visibility into the user's journey.
Identity orchestration connects all components into a manageable flow
At its core, an identity orchestration platform connects all IDV components, workflows, and identity-related data, ensuring that identity-related processes are manageable, scalable, and consistent.
Orchestration acts as the coordination and decision-making layer that defines how, when, and in what sequence identity components are used within a workflow.
Its role is to centralize logic and decision flows, making it easier to adjust verification steps, tighten or relax controls, add manual reviews, or reuse prior verification results where appropriate.
- Practical example: Unifying document and biometric verification tools
A company uses two different IDV solutions: one for document authentication and another for biometric verification. The document check is handled by an in-house module, while the biometric selfie verification is outsourced to a third-party provider. These tools operate as separate systems without shared workflow logic or context.
As a result, users must first upload their ID document in one step and then complete the biometric check through another. There’s no shared context between the systems, and users often need to repeat steps or resubmit information as the verification results aren’t reused across steps where permitted. For administrators, tracking the user journey is fragmented, and errors are harder to detect.
This task becomes even more complex when the IDV system must make decisions based on different verification contexts, for instance, when low- and high-risk users enter the flow.
With a digital identity orchestration solution, the tools are not simply connected into a single workflow. When a user starts the verification process, the orchestration platform automatically determines which path to follow: when to trigger biometrics, when a document check is enough, how to reuse existing results, and how to handle exceptions and varying risk levels.

- Practical example: Creating a case-specific workflow
A company serving customer groups of different ages needs to implement age verification checks into its current IDV flow under new age assurance policies.
It purchases a third-party age verification solution hosted in the cloud, which now must be integrated into the system.
With the orchestration platform, the company can set up this check only for underage users based on age attributes extracted during verification. During document verification, the IDV software automatically captures the holder’s date of birth from their ID and flags when a custom workflow with an additional age check is needed, considering the particular business process or regulation.

Get the most out of Regula IDV Platform
Full identity lifecycle management is at the core of the Regula IDV Platform, a unified identity orchestration solution that combines the functionality of proprietary Regula SDKs for document and biometric checks with workflow, identity management and built-in support for various compliance tools. At the same time, it remains 100% vendor-agnostic, allowing effortless integration with your existing tech stack and third-party systems via customizable connectors.
Here are more features you’ll get:
Instant start with ready-to-run components: Collect and transmit identity data to your systems, whether the platform is hosted on-premises or in the cloud.
Configurable orchestration with reusable scenarios: The platform includes industry-specific pre-configurable workflows that can be tailored to your identity orchestration use cases.
Compliance with KYC/AML and data protection requirements: The platform is designed to support KYC and AML processes and align with data protection frameworks such as GDPR and CCPA. It enables integration with customer screening services, including sanctions and PEP screening providers, watchlists, and other authorized data sources, where required.
User data management & analytics: Store and reference identity verification data within controlled workflows to support monitoring, auditability, and process improvement. Detailed logs of identity-related interactions and decisions provide traceability across verification steps, helping teams review outcomes, demonstrate compliance, and refine identity checks over time.
Learn more about what digital identity orchestration software can do for you!