Biometric passports are no longer a novelty. More than half of all countries have already adopted them, marking a near-complete global shift.
Let’s take a step back to explore how we got here, highlighting the key milestones, core features, and the weak points that still affect biometric passport verification.
What is a biometric passport?
Biometric passports are the next generation of machine-readable travel documents.
Unlike traditional machine-readable passports, which only contain printed information and a machine-readable zone (MRZ), biometric passports also include an electronic chip. For this reason, these documents are also known as electronic or e-passports.
This chip typically stores the holder’s photo and sometimes fingerprints or iris data along with personal details like name and date of birth.

The 1999 Icelandic passport (left) had a layout similar to the current version (right), making both easy to recognize and read with OCR technology.
Each chip is secured using public key infrastructure (PKI), meaning the data is digitally signed by the issuing authority using cryptographic methods.
Thanks to the chip and its built-in antenna, biometric passports support contactless verification via RFID or NFC technology, which is widely supported by smartphones. This extends their use far beyond border and airport checkpoints. Today, biometric passports are commonly used for remote onboarding, such as opening a bank account, or passing through automated border control at smart e-gates.
The use of NFC technology in passport verification has also led to new terms. “NFC chip” is now widely used, alongside the more traditional “RFID chip.”
Subscribe to receive a bi-weekly blog digest from Regula
Why have passports become biometric?
As with machine-readable travel documents, the move toward biometric passports was driven by ICAO. In the early 2000s, ICAO introduced Doc 9303, a set of standards defining the data formats and communication protocols for e-passports pursuing global interoperability goals.
One of the key pillars of this system is the PKI, which ensures that any ICAO-compliant passport can be verified by any compliant inspection system worldwide. This allows border authorities to quickly and securely check e-passports issued by other countries, improving both security and the passenger experience.
Malaysia was the first country to launch a biometric passport back in 1998—but without ICAO-standard PKI, those early chips weren’t compatible with global systems.
Unlike MRZs, which are now mandatory for all ICAO-compliant documents, embedding chips remains optional. However, in some regions like the European Union, adding biometrics (photo and fingerprints) has been legally required since 2004 for all member state passports.

Most biometric passports from EU member states have a burgundy cover. Shown here is Estonia’s 2021 edition.
What are the key features of biometric passports?
Biometric passports share a similar layout and overall design with other ICAO-compliant travel documents, but they come with distinct features mandated by Doc 9303.
The most visible sign is the “chip inside” symbol on the cover. ICAO standards require this emblem, and it’s also recommended to place it on the datapage. Its presence confirms that the passport meets ICAO requirements for electronic travel documents.

The Turkish biometric passport features the chip symbol on the cover only.

South Korea’s biometric passport includes the chip symbol on both the cover and the data page.

Biometric passports must also include an attention message on the page where the chip is embedded. Shown here is a 2006 passport from San Marino. However, chips can also be embedded in the cover or data page.
Another key feature lies within the chip’s data structure. It must follow a specific format, storing all required information in an organized structure. A digital photo is mandatory; fingerprints and iris data are optional, depending on the issuing country.
Beyond personal information, the chip also contains built-in security mechanisms—such as access control, digital signatures, and authentication protocols—ensuring the integrity and verifiability of the data.
Why are chip standards so important?
Just like the standard layout or MRZ, a chip with a specific data structure helps streamline the use of e-passports for identification worldwide. It allows inspectors—whether at border control, hotel reception, service desks, or even within mobile apps—to follow the same process for reading and verifying the stored data.
Using a standardized approach also helps build a chain of trust between passport-issuing authorities. This consistency is a key global measure for fighting document fraud.
What is the process of biometric passport verification?
The key difference between machine-readable and biometric passports is the embedded chip. This chip adds an essential step to the standard verification process.
Chip verification involves two main parts: data access and authentication. Several access protocols can be used for reading the chip, including:
Basic Access Control (BAC)
Password Authenticated Connection Establishment (PACE)
Extended Access Control (EAC)
In practice, these protocols rely on cryptographic methods—either symmetric or asymmetric. To access the chip, data from the MRZ or Card Access Number (CAN) is used, depending on the protocol.

The 2024 Dutch biometric passport displays a CAN on the datapage. This number is used during chip verification.
Once access is granted, the chip’s authenticity can be verified using one or more of the following methods:
Passive Authentication
Active Authentication
Chip Authentication
Terminal Authentication (used only by public authorities)
For instance, Passive Authentication verifies the integrity and authenticity of the chip data by checking digital certificates.
When an e-passport is issued, the Country Signing Certificate Authority (CSCA) private key digitally signs the Document Signer (DS) Certificate. The DS private key then digitally signs the chip.
During verification, the chip’s signature is checked against the DS certificate, and the DS certificate’s signature is verified against the CSCA certificate provided by the issuing country’s authority. If all links in this chain are valid, the chip is considered authentic.
Why are security certificates so crucial for chip verification?
One of the main interoperability challenges is the need to trust passport data from many different issuers. Each e-passport’s chip is digitally signed by the issuing country, and verifying that signature requires access to the country’s public key or signing certificate.
Typically, countries upload their public keys to a central repository—the ICAO Public Key Directory (PKD)—where other authorized parties can retrieve them. An alternative source is Germany's Federal Office for Information Security (BSI), which also distributes certificates globally.
However, not all countries are equally willing to share their signing certificates internationally. Some nations don’t publish their public keys in the PKD, which makes it harder or even impossible for foreign systems to validate those e-passports.
What can go wrong during e-passport verification?
Under normal conditions, biometric passport verification takes just a few seconds. However, several factors can cause delays:
Slower process
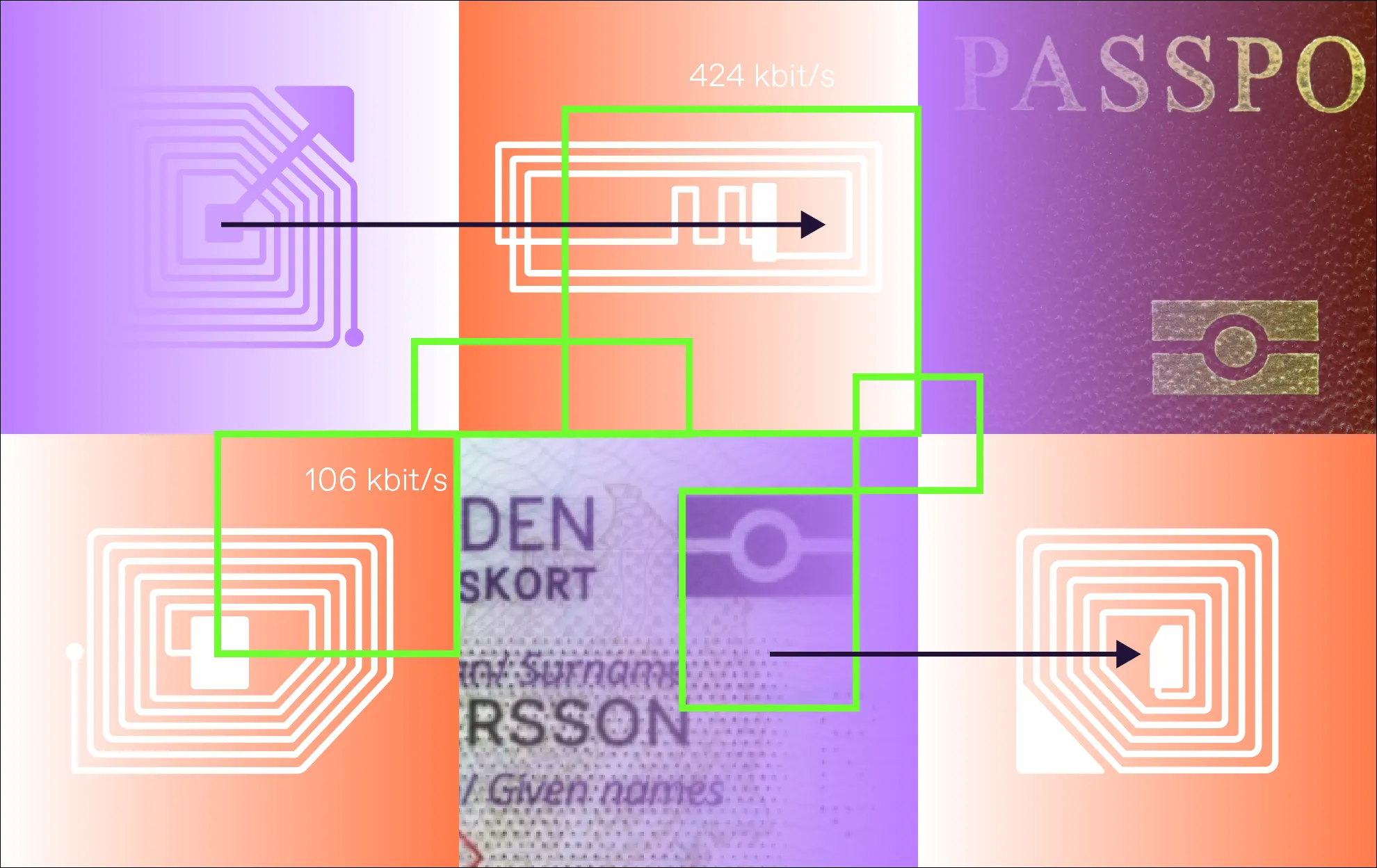
Chips in different biometric passports differ in several technical characteristics, including bit rates for data transmission. This directly affects speed. For instance, chips that support Very High Bit Rates (VHBR) offer greater storage capacity and significantly faster data exchange.
The access protocols used also impact performance. E-passports using PACE enable more efficient key exchange than those using the older BAC.
Finally, verification software settings matter. Some chips support extended-length reading for handling larger cryptographic objects. If the software is misconfigured and tries to use this feature with chips that don’t support it, the verification process can slow down or even fail.
Chip data format
To ensure global interoperability, biometric data stored on e-passport chips must follow international encoding standards, which are periodically updated.
A key example is the shift from ISO/IEC 19794:2005 to ISO/IEC 39794, which became the recommended standard in August 2023.
The updated standard allows for more detailed metadata to be recorded, such as facial landmarks, as well as more precise attributes like eye and hair color in the holder’s portrait.
Under current guidelines, e-passport issuers must adopt the new standard by 2030, while IDV vendors should support chip reading with photos encoded in accordance with the new format by 2026.
Chip-related fraud
As e-passports become more common, fraud tactics are evolving too. One of the most sophisticated threats is chip cloning, where scammers copy the contents of a legitimate chip and present them during NFC-based verification.
To counter this, chip verification procedures include protective features like Active Authentication and Chip Authentication, which are designed to detect cloned chips. What’s more, Chip Authentication is considered stronger, so some e-passports, like German ones, don’t support the Active Authentication mechanism at all.
However, there’s a catch: these mechanisms assume the use of trusted devices—something that’s not guaranteed when users verify documents on their own smartphones. In such cases, fraudsters can exploit vulnerabilities and manipulate verification results.
That’s where server-side reverification becomes critical. Here, the actual verification happens on the company’s secure server, while the user’s device functions only as an e-passport reader. The server generates session keys, decrypts the data after the chip is read, and keeps all information within a secure environment. This allows companies to re-access and reverify the data at any time.
This approach is already implemented in Regula Document Reader SDK.
What are the best practices for biometric passport verification?
Given the challenges and scenarios discussed above, what can businesses do to make the most of biometric passports in their operations?
Keep your verification system up to date: Your solution must fully comply with ICAO Doc 9303 and keep pace as the standards evolve. This includes supporting required cryptographic protocols (BAC, PACE, EAC) and handling the latest data formats. Regular updates ensure compatibility with new passport series and features.
Manage certificates and keys: To reliably authenticate biometric passports worldwide, maintain a current repository of country signing certificates. Join the ICAO PKD or use a service that supplies verified public keys. For countries not in the PKD, establish bilateral channels to obtain certificates. This helps prevent false rejections due to “unknown issuers” and boosts protection against forged or cloned chips.
Strengthen anti-fraud measures: Your software should support complete chip verification using all available authentication methods. A zero-trust approach to mobile devices is essential to ensure verification results from third-party readers aren’t modified.
Invest in testing: Test your solution with a wide variety of passports to confirm it works with the documents your users carry. Fine-tune system parameters like chip reading speed and ensure mobile-based NFC reading works reliably across the common smartphones used by your audience.
Tip: Regula offers NFC TestKit for enterprise-level testing with a broad range of real-world e-passport samples.
Have more questions about biometric passport verification? Let’s talk—book a short intro call to discuss your specific case.



.webp)