Now, customers can do almost everything online—from opening bank accounts to completing flight check-ins. Importantly, they can do this using their smartphones and easily authenticate through fingerprints or selfie verification.
In this article, we’ll delve into the process of digital identity verification with real examples from different companies, in an attempt to discover the most optimal flow.
What is digital identity verification?
Digital identity verification is a remote-first procedure aimed at confirming that an individual is who they claim to be.
In real life, the digital identity verification workflow may have many different presentations. Some businesses offer customers the option to complete the procedure on their own. Others add human agents into the loop who play the role of “online inspectors” and guide the client during the check. Video interviews, where the client must show their photo ID next to their face to the camera, are one example illustrating this semi-automated approach.
Despite digitalization gaining momentum in various sectors, digital identity verification isn’t a common option yet. What’s more, the requirement to confirm customers’ identities primarily affects companies in regulated industries operating under mandatory Know Your Customer policies.
Usually, this procedure is included in business-customer interaction in Banking, Fintech, Crypto, Aviation, Government, and many other sectors where it’s critical to ensure the person is real and not a scammer or other bad actor.
Here are some common use cases when customer verification is needed:
Customer onboarding
Purchasing airline tickets and completing the check-in process
Accessing particular services or features available on a platform
Confirming transactions in real-time
Account verification for contractors in gig economy services
We’ll deliver hand-picked content from Regula’s experts into your inbox
Components of digital identity verification
To ensure that a legitimate user is on the other side, companies apply different methods. A customer’s identity can be verified by checking the legal information available in official databases held by credit bureaus, government bodies, mobile operators, etc. Authentication of users’ government-issued ID and/or biometrics is another conventional method.
Most digital identity verification systems are based on one or both of the following determinants:
- ID document verification: Confirming the submitted ID is authentic and belongs to the user who presents it.
- Biometric verification: Confirming the user is a real person and who they say they are.
How these two elements look and fit together in practice is constantly evolving. Manual checks of ID scans uploaded by a user are increasingly replaced with automated authentication checks. Facial recognition technology, made popular by Apple’s Face ID functionality in 2017, continues to improve year-on-year, becoming a reliable defense in identity and access management.
When summarizing all existing options to verify customers online, we can create the matrix like this:
| User identifiers | Channels | Tools | Technologies |
|---|---|---|---|
|
|
|
|
Companies mix these technologies and methods to build a robust verification process. Let’s see how this looks in practice by observing some methods harnessed by organizations worldwide.
Real-world examples of digital identity verification from various industries
Neobanks that don’t have physical branches are among the businesses where online identity verification is a cornerstone. Typically, they make the verification procedure a must for all new clients. The onboarding workflow varies from company to company.
Chime from the US requests only essentials, such as an individual’s name, address, and Social Security number (SSN). They then validate these personal details against trusted databases before granting full access to their services.
Monzo from the UK requires all new users to submit an ID scan and take a video selfie to sign up. During verification, identity attributes (biometrics) and a proof of identity (ID) is analyzed and matched.

Two neobanks—Chime and Monzo—rely on different verification methods for onboarding new customers.
Sometimes, digital customer verification involves users filling out application forms where they provide additional facts confirming their identity.
For instance, all new educators on Pearson, a digital educational platform, must provide detailed information about their occupation, as well as personal details and an ID, to complete the verification process. This expands the number of trusted sources for the company, as they can reach out to the mentioned educational institution to ensure the user really works there.
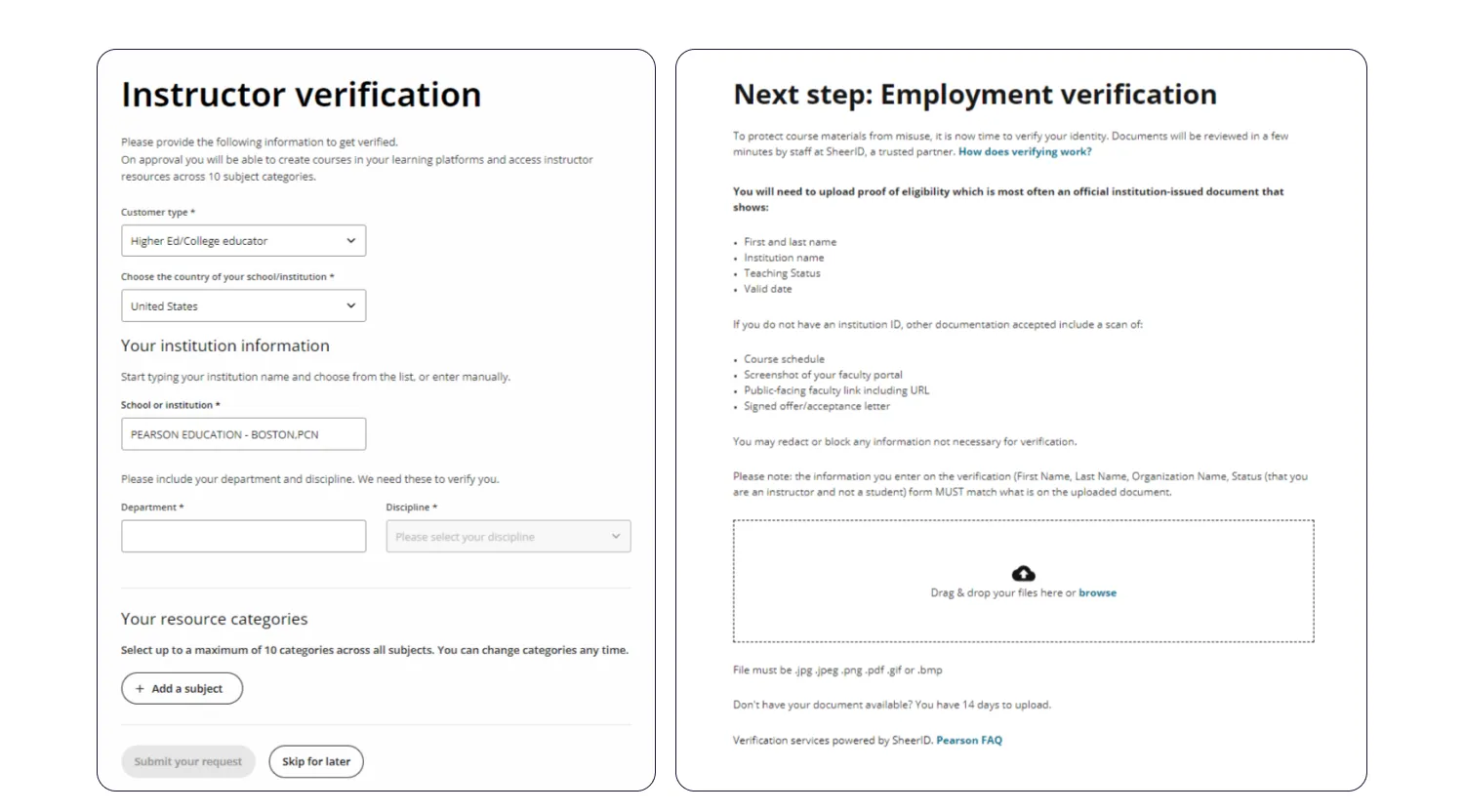
Requesting additional information from the user enables organizations to create a more transparent verification process.
The “selfie+ID” matching can sometimes be replaced with cross-checks involving other individual characteristics. Ryanair is an example.
The company asks all customers booked flights via a third party and not directly through its official website or application to verify their booking and identity before travel.
In addition to express verification where the passenger’s ID and selfie are needed, they provide the standard verification flow. In the latter case, the photo of the passenger’s signature is matched with their ID, which includes the signature. Both procedures also require the confirmation of phone number and payment details from the user. The passenger can freely choose between these two options.

Ryanair can verify passengers in two ways, including by matching their signatures with those on an ID document.
Sometimes there are three mandatory components in the digital ID verification process. According to KYC regulations, proof of address is also needed in addition to a valid government-issued ID and a selfie.
Cryptopay, a crypto management platform, requests additional documents to verify the user’s residency. However, the same ID document can’t be used as proof of identity and proof of address simultaneously.

Official documents containing personal information can also be used in digital identity verification.
Digital ID verification is widely used by companies that hire many gig workers for operations such as goods delivery from local shops. This is exactly what Instacart does.
To sign up as a full-service shopper, a user must be 18 or older, eligible to work in the US, and have access to a vehicle for deliveries. For verification, the company requests a photo of a driver’s license and a valid credit card.
Interestingly, Instacart asks all new workers to block the identification number and date of birth on their ID, as well as block all credit card details except for the name and the last four digits, for security purposes.

Gig workers may also be asked to submit valid credit card information to receive payment for completed orders during the verification process.
Sometimes digital ID verification is an additional step. This mechanism is used by the British National Health Service (NHS).
All users who want to access digital NHS services, including online pharmacies and consultation services, must set up an NHS login. Additionally, to view their health records or any personal information, users are required to provide proof of identity. Interestingly, if an individual’s mobile phone number matches the one they have registered with their general practitioner, the NHS will use it to verify the patient’s identity. Otherwise, a passport, driver’s license, ID card, or other photo ID, along with a selfie, is needed.

Users of the NHS online services can choose how to verify their identity.
The emergence and widespread use of electronic identity documents with RFID chips have enabled businesses to create more secure digital ID verification systems. For instance, SEB, a leading Nordic financial services group, only accepts e-documents during customer onboarding in its Smart-ID app, which serves as proof of identity for accessing the internet bank.

To submit a biometric ID, a user must scan an RFID chip using their NFC-enabled device. SEB provides customers with clear guidance on how to complete the process.
As a secure and digitally signed asset, an RFID chip embedded in biometric passports and ID cards offers high resistance to fraud. It can be scanned with any NFC-enabled device and quickly verified with most IDV solutions.
Some companies, including SEB, use biometric identification as a form of incentive for clients. For instance, the bank’s customers in Latvia and Lithuania can upgrade from a Basic account to a more advanced level, which grants them access to e-services, digital signing, and more.
The next significant development in digital identity verification is the widespread adoption of Digital ID, a digital entity stored and accessed online. Although this concept is relatively new in terms of digitizing government-issued IDs, third-party digital identities, such as Apple ID or Microsoft ID, are already used by some businesses for customer identification purposes.

KAYAK, a metasearch engine for travel services, offers Apple ID as one of its sign-in options.
What path to take when choosing the right solution for digital identity verification
There is no flawless way to verify customers online. When deciding on the approach, you should balance user comfort with security.
Processes that require active user engagement—such as active liveness checks or completing multiple application forms, often seem less smooth and user-friendly. However, these additional checks contribute significantly to security.
Unfortunately, defenses can be bypassed using fraudulent tactics. For instance, bad actors can create a synthetic identity using a stolen SSN to sign up. Additionally, they can deceive systems with sophisticated deepfakes and AI-generated identity documents.
Finally, customers from certain target groups may experience difficulties with digital ID verification. This can result in more unqualified ID scans, such as those taken in poorly lit rooms or at incorrect angles, leading to frustration for customers.

Digital ID verification can sometimes be a challenging process for customers.
Thus, you need to consider both UX and security aspects, as well as meet all the KYC requirements associated with your industry.
At Regula, we offer a fully customizable, 100% in-house solutions for seamless ID and biometric verification based on face recognition:
Regula Document Reader SDK: With an ID template database of over 16,000 items from 254 countries and territories, it provides enhanced security for all sectors, including regulated industries.
Regula Face SDK: Offers a reliable customer biometric verification to prevent a wide range of presentation attacks.
Get in touch with us to learn more about how we can implement a robust IDV solution tailored to the needs of your company.






