Imagine arriving at an international airport. As you pass through immigration, your passport is swiftly scanned, confirming your identity in seconds. This seamless process is thanks to RFID-chipped passports, which the International Civil Aviation Organization (ICAO) standardized in 2006.
In this article, we'll guide you through the key aspects of RFID chips in electronic IDs:
What is RFID and how does it work?
What information do RFID chips contain?
How to ensure that a chip is genuine?
Onwards!
What is RFID technology?
RFID, which stands for Radio Frequency Identification, uses radio waves to transfer data and identify objects. With an RFID reader or scanner, you can receive information about an RFID-tagged item from a distance. The technology is often used in Retail to conduct inventory checks and conveniently locate items in stores and warehouses.

Basic radio frequency identification workflow
The data is stored on an RFID tag or microchip—a small electronic device embedded in or attached to an item—and is transferred through antennas, which both the item and the reader are equipped with. While the tag is a passive asset that transmits information “upon request,” the chip can interact with the reader in a “dialog” manner.
RFID uses depend on the frequency
Data exchange between an RFID tag and a reader occurs at different frequencies. Here are the three most commonly used:
Low frequency (125 KHz): Used in access control systems (key fobs, pass cards) and animal tracking.
High frequency (13.56 MHz): Used in electronic identity documents (passports, ID cards, driver’s licenses) and payment systems.
Ultra-high frequency (840-960 MHz): Used in logistics, manufacturing, retail, and electronic toll collection systems.
The frequency determines the read range, data transmission speed, and available data exchange protocols. For instance, high-frequency RFID chips in electronic IDs have a read range of 1-10 centimeters, while ultra-high frequency RFID tags can be read from up to 100 meters away.
Get posts like this in your inbox with the bi-weekly Regula Blog Digest!
Using RFID chips in identity documents
The first attempt to use RFID technology in identity documents was a Malaysian electronic passport issued in 1998. At that time, even specifications for this technology didn’t exist.
Later, in 2003, the ICAO updated Doc 9303, the standard for countries issuing machine-readable travel documents (MRTDs), including electronic passports. In this document, an RFID chip is referred to as a "contactless integrated circuit" (CIC). This semiconductor device stores data and communicates with a reader through radio frequency energy according to the ISO/IEC 14443 standard.
There are also separate standards that define the use of CICs in other types of electronic identity documents. For instance, the ISO 18013 series is dedicated to driver’s licenses.
According to current guidelines, the "chip inside" emblem must be visibly present on either the front cover and/or the personal data page for all electronic identity documents.

All electronic ID documents have the “chip inside” emblem
How does RFID work in identity documents?
The RFID verification flow looks simple from the user’s perspective. You scan the RFID chip with a specialized reader or NFC-enabled smartphone. The device creates an electromagnetic field with its antenna that powers the chip inside the document, so it can communicate with the device. Then it sends some commands to obtain the required data. The chip “replies” with the requested information. Finally, you can see the results via the particular application you use.
The technical part of RFID verification is more complicated. (We’ll get back to it further in the article.) Simply put, the chip is a data medium. It includes an operating system to access the data and applications like ePassport, eID, eDL, eSign, and others.
Under the ICAO standard, biometric passports, ID cards, residence permits, etc., may contain RFID chips with the ePassport application.
What information does an RFID chip store in the ePassport application?
The content of RFID chips varies depending on the type of identity document. However, different data is always stored separately, and each file has its own unique identifier which is used to provide access to it. This segregation contributes to RFID chip security.
Typically, there are informational and service data packages.
Information data groups in an RFID chip
For instance, a biometric passport’s chip includes the following data groups (DG):
DG1: Basic personal information, also encoded in the document’s machine-readable zone (MRZ): name, date of birth, nationality, sex, etc.
DG2: Holder’s photo
DG3: Fingerprints
DG4: Iris scans
DG5: Additional photo of the holder in higher quality
DG7: Image of the holder’s signature
DG11: Additional details on the holder beyond MRZ data, such as date of issue, full name or the name recorded in a local language, place of birth, etc.
DG12: The information on the issuing body: where, when, and by whom the document was issued
DG13: Additional details reserved for use by the national services of the issuing state
DG14: Information about cryptographic algorithms and a public key used for Chip Authentication (CA)
DG15: Information about cryptographic algorithms and a public key used for Active Authentication (AA)
DG16: Information about persons to notify in case of emergency
Data groups DG6 and DG8-DG10 are reserved for further standard development.
This structure makes it possible to set different access levels to the data recorded on the RFID chip. For instance, the DG2 file with the document holder’s photo is checked during routine verification sessions like customer onboarding in a bank. However, only authorized entities like border control or police officers can access biometric data, such as fingerprints stored in DG3. In some countries, such as Germany, the ability to read all the biometrics encoded in the chip is restricted to authorized entities.
Service data groups in an RFID chip
The service data groups contain files for secure data access procedures, digital signatures, and chip authentication algorithms. One of the core files from this cohort is the Document Security Object (SOD).
Generally, the SOD holds hashes of all data groups that map data of any size stored on the chip to fixed-size values, a digital signature generated during the document personalization stage by its issuing body, and the issuing authority certificate (Document Signer Certificate). All data in data groups is recorded in ASN.1 format.
Hashing helps turn data from informational data groups into impersonal unique values that don’t expose any sensitive details. For example, DG1’s hash may look like:
“8743b52063cd84097a65d1633f5c74f5”
Since hash strings have a specified length, a data group can be even shorter than its hash.
The SOD is also digitally signed to prevent fraudulent alterations.
How is data secured on an RFID chip?
The backbone of protecting confidential data within a chip is cryptographic algorithms. They transform plain text into a ciphertext that looks like a jumbled mess to anyone who might intercept it. This can be done using symmetric or asymmetric cryptography. Both mechanisms are involved in protecting RFID chips.
Symmetric cryptography uses the same key (a shared secret) for “packing” and “unpacking” incoming and outgoing messages. Since the secret key is available to both the sender and recipient, this method is less secure than asymmetric cryptography.

Asymmetric cryptography uses two pairs of mathematically related keys: a private key for encryption and a public key for decryption. The public key is available to both parties, but only the message recipient has access to the private key. This makes asymmetric algorithms more reliable.

Generating digital signatures in RFID chips relies on asymmetric cryptography. The private key is used to create a unique signature attached to the message. The corresponding public key, available to the recipient, verifies the signature's authenticity, ensuring that the owner of the private key generated it.
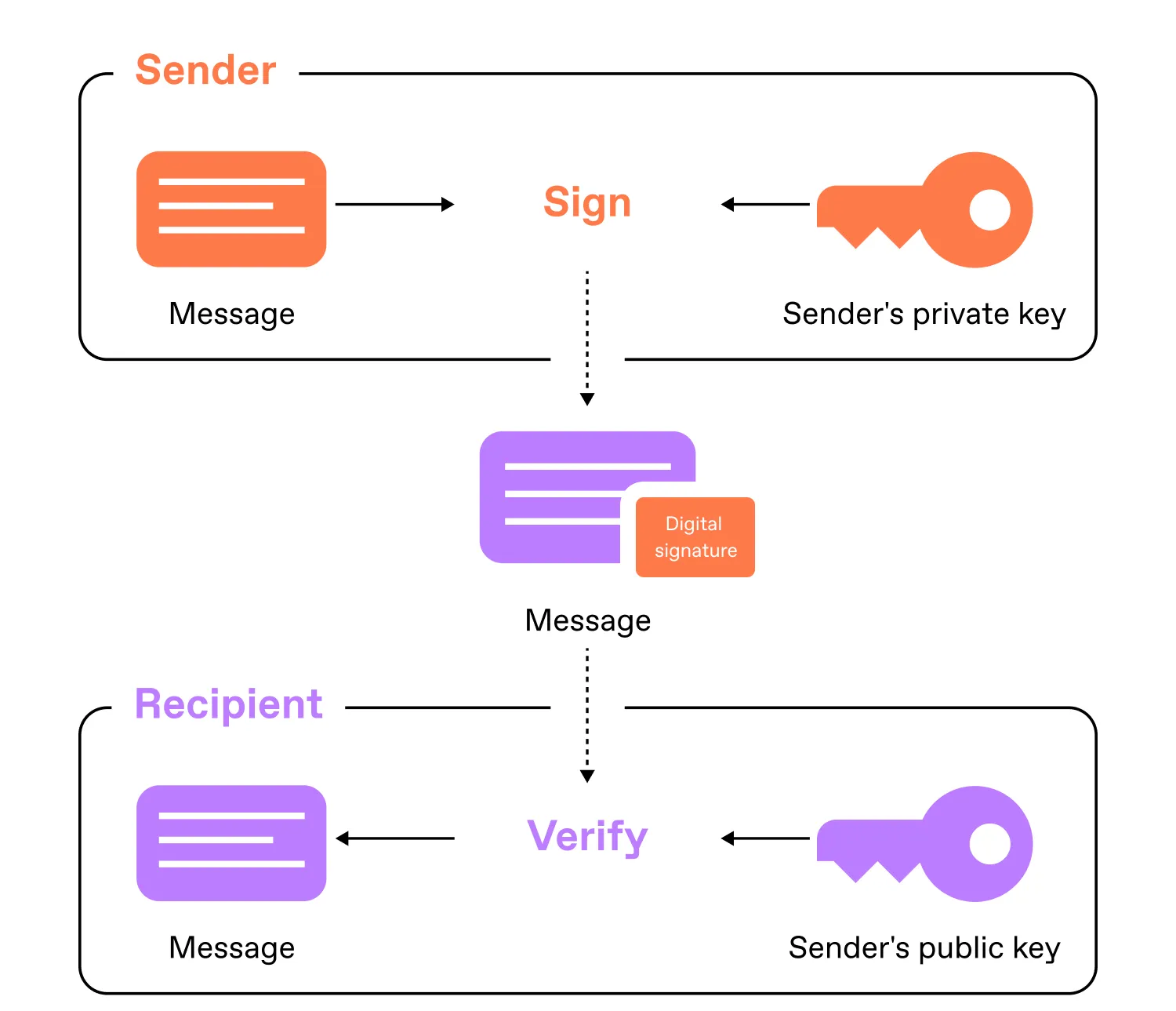
The identity document issuing bodies—the country’s authorities—cryptographically sign chip content in newly issued documents with a digital signature using the private key. However, the entire data set is not signed; only a hash is calculated based on it. To ensure accuracy and reliability, a hashing algorithm of sufficient length is used.
The process follows these steps:
Specific data is selected, based on which the hash will be calculated.
The hash is calculated.
Using a pair of keys, a signature from the hash (or multiple hashes) is calculated. The public key is placed in a DS certificate, and the certificate is further signed by CSCA following the same process.
Certificates containing the public key required for verifying data are distributed to the relevant parties.
Trusted certificates
Each country that issues electronic identity documents also generates corresponding security certificates: the Country Signing Certification Authority (CSCA) Certificate, and the Document Signer Certificate (DSC). The CSCA private key digitally signs the DSC, and the DSC private key digitally signs the SOD in the chip. Together, these signatures establish a chain of trust.
Many countries exchange their certificates with each other directly or through the ICAO Public Key Directory (PKD), the centralized certificate catalog. This makes it possible to verify foreign electronic documents at any border control point. Another option is the German certificate catalog run by the BSI (the Federal Office for Information Security), which has alternative country coverage.
However, some countries (usually less prosperous ones) don’t participate in certificate exchange. Since many of these regions also contribute to illegal migration, verifying electronic documents issued by their governments remains a significant challenge.
How to access an RFID chip
To protect the privacy of electronic identity document holders, information stored on an RFID chip is secured with an access control mechanism. This mechanism prevents data from being read unless the inspection system, such as a passport reader at an airport, can prove its authorization.
This helps prevent eavesdropping on the “dialog” between the chip and the reader, and stops fraudsters from skimming the data using third-party scanners.
There are three forms of access control currently used in electronic IDs:
Basic Access Control (BAC)
Password Authenticated Connection Establishment (PACE)
Extended Access Control (EAC)
Basic Access Control (BAC)
BAC is one of the earliest methods to secure communication between chip and reader, but it’s still in use today. The reader obtains the secret key for encrypting/decrypting transmitted data from the document's MRZ code, which is derived by combining some lines. This method allows the terminal to access the chip only if it confirms the document's physical presence: it verifies if the MRZ data in the visual inspection zone (VIZ) matches the data stored on the chip.
The downside is that BAC relies on symmetric cryptography, so it can be vulnerable to attacks if the key is compromised. Moreover, the MRZ is not so unique that it cannot be guessed. Some countries, like Germany, have stopped issuing biometric documents compatible with the BAC protocol in favor of other methods like PACE.
Password Authenticated Connection Establishment (PACE)
Unlike BAC, the PACE method uses asymmetric encryption to provide stronger protection. The process itself remains similar, following the logic of BAC. PACE uses either MRZ code fragments or a Card Access Number (CAN).
Extended Access Control (EAC)
EAC provides extra security for sensitive biometric data like fingerprints and iris scans stored on the chip and permits only authorized terminals to access this data. Introduced as an additional security layer to BAC, it’s optional for inspection systems if biometric data reading is not required during identity verification.
Typically, EAC is addressed through the combination of two specialized authentications:
Chip Authentication
Terminal Authentication
We’ll describe both of them, along with some other methods, below.
The types of RFID chip authentication
The RFID verification flow is determined by the issuing country, the specific use case, and the identity verification software in use. There are four methods to authenticate the chip:
Passive Authentication
Active Authentication
Chip Authentication
Terminal Authentication
All of the methods may be used in business operations, save for Terminal Authentication—in most cases, it is available only to authorized entities, such as law enforcement agencies.
Document Reader SDK can be used to execute any of the four procedures.
Passive Authentication
The purpose of Passive Authentication is to confirm the integrity and authenticity of the data stored on an RFID chip. Here’s how it works:
The mechanism engages the service data package (SOD), where the hashes of the data groups are located.
The SOD is cryptographically signed with a digital signature generated at the ID document issuance stage. The document issuing authority does it with the use of the DSC and the corresponding CSCA certificate; both are also digitally signed.
In this scenario, the DSC holds a public key used to validate the SOD, while the CSCA holds a public key used to validate the DSC.
Since the CSCA is self-signed, its signature can be verified using the public key contained in the certificate itself. The certificates are available in the ICAO PKD, as well as other trusted sources.
The authenticity of the information data groups is verified by comparing the computed hash values of the data groups’ content with their respective counterparts stored in the SOD. If all components, including the cryptography algorithms and SOD structure, are consistent, the data in the RFID chip is considered genuine.
Active Authentication
Active Authentication aims to verify whether the chip is genuine and not a clone. The method requires a challenge-response exchange between the reader and the chip using asymmetric cryptography.
Here’s how it works:
During active authentication, the reader generates and sends the chip a random “challenge” (control piece of data).
The chip digitally signs the “challenge” using the private key and sends it as a “response”.
The private key is stored in the protected memory of the RFID chip and cannot be read from outside. The reader verifies the validity of this digital signature using the public key from DG15 (for electronic passports) or DG13 (for driver’s licenses) and identifies the chip as authentic only if the returned signature is correct.
Nowadays, Active Authentication is used less; it is being gradually replaced by Chip Authentication, which is a more reliable mechanism.
Chip Authentication
The Chip Authentication procedure is an improvement over Active Authentication, as it uses more advanced cryptographic algorithms. By using two pairs of public and private keys, it employs a shared secret key accessible to both parties involved in the process. This serves two purposes: establishing secure messaging between the passport and the reader, and protecting against chip cloning.
How it works:
The chip and the reader exchange their public keys to mathematically derive the secret key using their private keys as a required part of the calculation.
The private key is recorded on the chip during the production of the biometric ID and is available for reading from “inside” only. DG-14 contains a public key and a crypto scheme for calculations.
If the RFID chip data is copied to another chip, its private key will change as well. As a result, the secret key calculated on the chip’s side won't match the one derived by the reader, which may point out chip alterations.
Terminal Authentication
Terminal Authentication follows Chip Authentication under the EAC protocol. The goal is to prevent unauthorized terminals (readers) from accessing sensitive data stored on the RFID chip, primarily biometrics. Successful terminal authentication also enables authorized parties to update the information stored on the chip.
It works like this:
The RFID chip and the terminal engage in a mutual verification process. The chip sends a challenge to the terminal. The terminal must respond with a signed response based on the cryptographic keys stored within it to prove its legitimacy.
The response is encrypted using cryptographic algorithms and shared keys to ensure secure communication.
If the terminal’s response is verified, it gains access to the sensitive data on the chip.
Can fraudsters fake RFID verification results?
The chips in electronic documents are usually verified with specialized devices that support RFID reading and verification, such as passport readers. These devices are an essential element in creating a secure digital perimeter.
With the growth of digital onboarding in Banking, Healthcare, Aviation, and other industries, many sessions involving RFID verification are now conducted remotely. In remote scenarios with identity verification apps, users’ mobile devices supporting the NFC protocol are used as chip readers. This is generally a reliable practice, but unfortunately, there’s a loophole for fraudsters.
All RFID chip authentication mechanisms were developed with the idea that the readers used were trusted devices. That was true in the early 2010s. Over time, as more people used smartphones, they became an optional part of the inspection process in addition to authorized passport readers and ID scanners.
The problem is, fraudsters can generate positive NFC verification results during a mobile session. They can also present a genuine passport equipped with an RFID chip containing information cloned from someone else’s document.
This means that counterfeit documents submitted online might be mistakenly verified as valid.
The solution? Never trust RFID verification results obtained from a remote source
To prevent chip verification results from tampering, we use server-side RFID verification based on the “zero-trust to mobile” approach. This additional re-check ensures that the chip is authentic, not a clone, and contains original data.
Here is how it works with Regula Document Reader SDK:
Once the chip is read on the user’s device, the RFID chip data is transmitted to the server.
Then, all the data is rechecked within a trusted perimeter. During the CA/AA process, Regula generates keys for the transaction on the server, which are sent to the client to perform specific operations, and then used to check that they are valid on the server compared with the received data.
If any mismatches or fraudulent traces are detected—e.g., the use of different cryptographic schemes, digital signatures based on expired or faked DSCs or CSCAs—the collected data or the chip itself was likely tampered with during the initial verification.

During server-side verification, the user’s mobile is not a trusted source; it’s just a data transmitter. To verify that the RFID chip authentication process is carried out accurately, the results of mobile verification are re-examined within a secure perimeter.
You can make server-side RFID verification a mandatory part of your online identity verification flow. It also can be a way to conduct additional checks upon request. The outcome of each mobile authentication session is securely saved on your server, giving you the option to revisit them later if needed.
Importantly, all of this occurs solely within your premises; no third parties, including Regula, have access to the data.
Take security to the next level with RFID verification
Many businesses are adopting RFID verification of electronic IDs for online onboarding and/or authentication as a benchmark in identity verification. UBS, the largest private bank in the world, has completely excluded non-electronic passports from their interactions with new clients.
However, fraudsters never stop trying to cheat the system, so there’s no magic pill—even if it’s as powerful as server-side chip verification.
A reliable identity verification solution should examine each part of the document. For instance, you can compare personal information extracted from the RFID chip to the same data in the VIZ, MRZ, and barcode(s) in order to ensure consistency. Plus, there should be a complete set of authenticity checks, such as liveness detection and face matching.
When automation is involved, additional checks don't create any friction for your customers. As a result, you avoid sacrificing customer experience while keeping your perimeter secured.
💡Feel free to explore our guide on how to choose the most reliable identity verification solution, where we cover this in detail.






