Verifying identity documents with electronic chips is often the most convenient option for users, especially in remote scenarios. The main advantages are speed and ease of use.
Companies appreciate this approach primarily because of its security, since cryptographically signed chips are hard to alter or counterfeit. It allows companies to confidently verify the identity of remote customers, even without meeting them in person.
But what really happens after an electronic passport is tapped on a reader, be it a smartphone or a document scanner? That depends on several factors, including the chip itself—something many businesses overlook when choosing NFC verification technology.
In this article, we’ll take a closer look at the technical side of chip processing to reveal:
What speeds it up
What slows it down
How to boost the process
Get posts like this in your inbox with the bi-weekly Regula Blog Digest!
The tech behind the chip in identity documents
The chip, formally known as a contactless integrated circuit, is a standardized security feature commonly used in electronic identity documents since the mid-2000s.
Technically, it is a smart card with an antenna. As a passive device, it has no battery. Instead, it relies on the electromagnetic field emitted by a reader, using technologies like Near Field Communication (NFC) or Radio-Frequency Identification (RFID). The reader generates a field that powers the chip and enables communication.
NFC vs. RFID
Both technologies use radio waves for wireless data exchange. The main differences are their communication type and operating range.
RFID can work over distances of several meters and typically reads data in one direction. NFC, a subset of RFID, is designed for close-range communication (about four centimeters or less) and establishes two-way, interactive data exchange.
In electronic IDs, short-range RFID at 13.56 MHz is the standard for data transmission using document readers, with an operating range of up to 10 centimeters. This frequency is also supported by NFC-enabled smartphones, which are now commonly used for remote document verification. So, both RFID and NFC are part of the process.
As an electronic medium, the chip runs an embedded operating system with a logical data structure containing separate data groups. Because the chip stores sensitive data, such as biometrics, its system is protected by cryptography and access controls. This prevents unauthorized reading, eavesdropping (interception of the chip-reader communication), and other attacks aimed at compromising chip integrity.
Also, after personalization (recording the holder’s data), most chip data groups are locked to prevent any additions. The exception is the Country Verifying Certificate Authority (CVCA) public keys used for chip verification—namely, for Terminal Authentication, which have shorter expiration terms (up to 3 years) than electronic documents. However, they can only be updated by authorized entities.
What are the guidelines for NFC verification?
The use of chips in identity documents, including issuance and verification, is regulated to ensure global interoperability of electronic IDs.
ICAO’s Doc 9303 sets the baseline specifications, primarily for electronic passports. It defines the chip's logical structure—data groups, security mechanisms, and the Public Key Infrastructure (PKI)—used for verification. Also, the ISO/IEC 18013 standard specifically describes the design format, data content, access control, and other characteristics of ISO-compliant driver’s licenses.
To securely access and read the chip, the system performs a series of “request-reply” operations based on the following access control mechanisms:
BAC/BAP (Basic Access Control/Protection)
PACE (Password Authenticated Connection Establishment)
EAC/EAP (Extended Access Control/Protection)
The overall process for all electronic documents follows transmission protocols outlined in ISO/IEC 14443. This standard also specifies the chip’s physical characteristics, radio frequency power levels, and signal interface requirements.
Regarding signal interfaces, two compliant options are available: Type A and Type B. While both support the same communication speeds, they differ in modulation methods (how data is encoded) and bit coding schemes. Type B chips, with their simpler yet faster signal handling, may offer better efficiency.
Additionally, other standards define core chip functions, such as command-respond structure, file management, access procedures (ISO/IEC 7816-4), and test methods (ISO/IEC 10373-6).
In this regulatory landscape, BSI TR-03110 stands out as a unique case. This document defines electronic IDs within the eIDAS (electronic Identification, Authentication, and Trust Services) framework—a system designed to support secure electronic interactions between businesses, citizens, and public authorities across EU member states. While some of the technical specifications of eID outlined in BSI TR-03110 overlap with ICAO’s standards, the document primarily focuses on eIDs in their fully digital form.
What affects NFC verification speed?
Even with detailed specifications in place, there’s no guarantee NFC verification will work the same across different platforms and devices. Importantly, many of the factors affecting the process are beyond the control of ID inspectors.
Let’s take a look at what those factors are.
#1 Chip characteristics
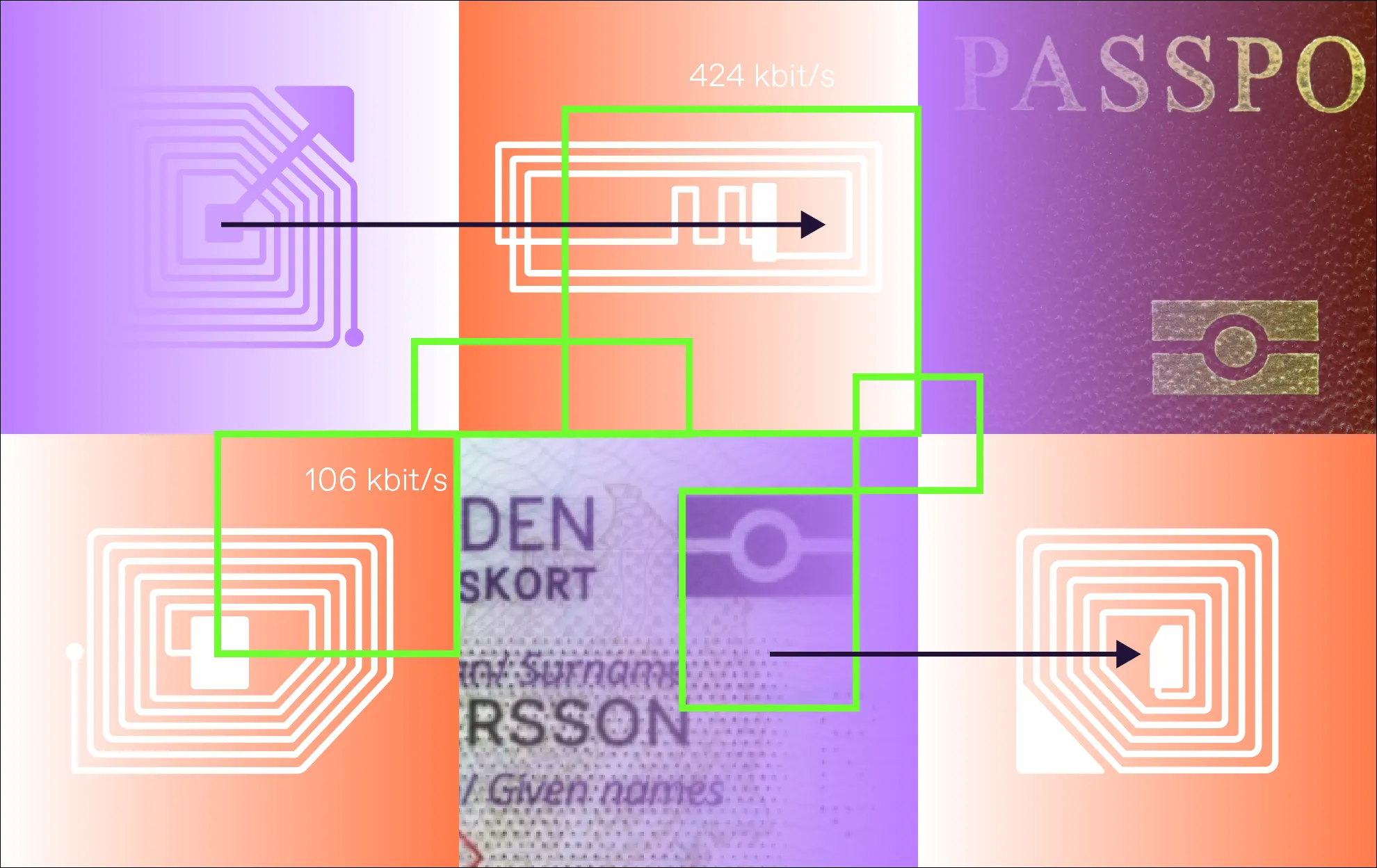
ISO/IEC standards and ICAO’s recommendations give electronic ID issuers several options regarding chips. For instance, there may be different bit rates for data transfers between the chip and the reader. While the mandatory speeds are 106 kbps and 424 kbps in both directions, devices can also support faster rates, including:
212 kbps
848 kbps up to 6.78 Mbps (both directions)
10.17 Mbps to 27.12 Mbps (reader to chip only)
Higher speeds support faster data processing and quicker biometric verification. Overall, upgraded chips deliver better performance than basic models.
A new generation of chips for electronic IDs
In 2012, chips supporting Very High Bit Rates (VHBR) were introduced in the ISO/IEC 14443 standard. These offer greater storage capacity and significantly faster data transmission—up to 6.78 Mbps—compared to traditional NFC speeds of 106, 212, or 848 kbps.
VHBR chips use the same modulation technique as slower ones, but their signal switches amplitude with every wave cycle. This requires high signal quality and precise performance from both the chip and the reader.
Regula’s hardware and software ID scanners are already equipped to support these advanced chips.
#2 Encryption methods
Processing speed also depends on the chip access protocol described earlier. These protocols are built on different cryptographic methods. For instance, BAC uses symmetric keys, while the more modern and secure PACE protocol relies on public-key (asymmetric) cryptography.
In practice, PACE enables more efficient key exchange between the chip and the reader. BAC derives keys using data from the machine-readable zone (MRZ) of an electronic ID. It forms a string from MRZ data, runs it through a hashing algorithm, and splits the result into two keys—one for encryption and one for message authentication.
PACE, on the other hand, uses a shared password (such as the MRZ or CAN) along with elliptic curve cryptography to create a secure session key. This allows the chip and reader to establish an encrypted, mutually authenticated connection. Unlike BAC, PACE doesn’t require hashing, which makes the process more efficient and secure, especially when both the reader and chip support high-speed data transmission.
The type of cryptography used also affects reading time, especially when the chip stores large data groups like facial images and fingerprints. Stronger encryption usually means longer keys and more complex algorithms, which take more time to process. During verification, each chunk of data must be individually encrypted before transmission. As the data is typically sent in 256-byte chunks, the chip has to encrypt each one separately—potentially hundreds of times. Since the chip is wirelessly powered by the antenna’s field, its processing capacity is limited, making encryption a time-consuming task.
To fix this, some chips support a feature called an extended length field. When available, the chip encrypts the entire data block once, then sends it in a single continuous transmission. This can reduce read time significantly—by half or even more—especially for large data groups with biometrics. For example, this is how it works with Regula Document Reader SDK:
| Comparison of chip verification speed (DG-2 Holder's photo), ms | ||
|---|---|---|
| Latvian ID card | ||
| 424 kbps | 848 kbps | |
| Standard | 4644 | 4379 |
| Extended | 1947 | 1754 |
| Irish ID card | ||
| 424 kbps | 848 kbps | |
| Standard | 1287 | 1163 |
| Extended | 640 | 495 |
| USA passport | ||
| 424 kbit/s | 848 kbit/s | |
| Standard | 1138 | 788 |
| Extended | 897 | 611 |
#3 IDV software capabilities
Given the wide range of chip technologies used in electronic IDs, terminals—specifically, the software they run—must handle various chip verification scenarios. In this context, “terminal” refers to any ID scanning solution, whether it is a hardware device or a mobile application.
According to ICAO Doc 9303, if the size of the cryptographic objects, such as public keys and signatures, exceeds the standard limits, Application Protocol Data Units (APDUs) with extended-length fields must be used to send this data to the chip. In such cases, the chip is required to support this feature, and this support must be clearly indicated, either in the Answer-To-Select/Answer-To-Reset messages or in the EF.ATR/INFO file.
Terminals, in turn, must support extended-length APDUs but can only do so after confirming the chip’s compatibility. This verification is done through the same data sources—ATR/ATS or EF.ATR/INFO.
But there’s a catch. Different IDV systems have different settings. For example, if the chip doesn’t support extended-length reading but the system tries to use it, the process may fail. In some cases, the system may fall back to standard-length reading, which is slower and increases the total session time.
Fortunately, this issue is becoming less common as more electronic IDs are built to support extended-length reading. If your business processes documents from a specific country, you can test this behavior and configure the system for optimal performance.
By the way, Regula Document Reader SDK, which is available for both mobile apps and hardware readers, supports all existing chip speeds and reading lengths, ensuring smooth NFC verification.
#4 NFC readers in mobile devices
Finally, the speed of NFC verification on mobile devices depends largely on the device itself.
While global standards set clear requirements for terminals, personal mobile devices fall outside that scope. For example, ICAO’s Doc 9303 only briefly mentions that electronic IDs should be compatible with NFC-enabled smartphones.
Also, smartphones have a wide range of tech characteristics, unlike standardized professional inspection systems. This creates several hidden pitfalls, like an antenna field that is too weak for a specific chip. As a result, NFC performance can vary significantly between devices.
There’s also an extra challenge related to user experience: the location of the NFC module varies from phone to phone. This may slow down the process for first-time users, who may struggle to find the NFC reader.
For example, the NFC area on all iPhone models is located at the top center and can be tapped from either the front or the back of the phone. On most Android devices, the NFC module is usually on the back, so electronic documents must be tapped on the back side only.
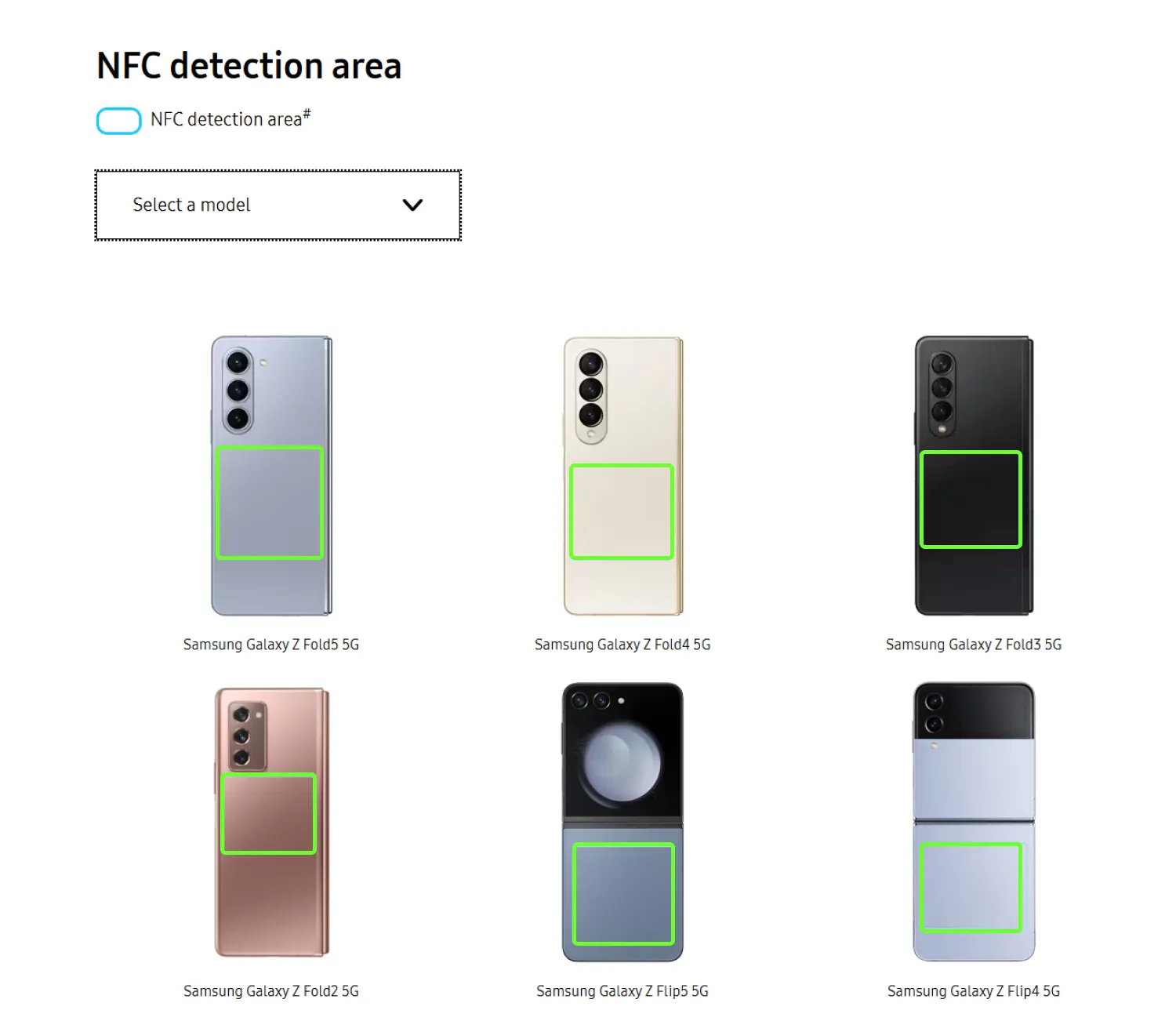
Some phone manufacturers offer visual guides to show where the NFC module is located on their devices.
In these cases, chip characteristics, such as support for extended-length fields or high processing speed, don’t influence the process. So, if you need smooth and reliable reading on mobile devices, the IDV app you use must be customized and configured to perform well under these specific conditions.
Test your electronic IDs with Regula SDK
As you can see, chip reading speed depends on many factors. That’s why the best approach when integrating an IDV system into your NFC verification process is to test several options first.
At Regula, we provide clear instructions on RFID chip processing using mobile devices, with separate guidelines for iOS and Android. Server-side verification is also available for added security.
Exclusively for enterprise-level customers, we offer Regula NFC TestKit, a service that provides a set of electronic IDs, personalized with either fictitious data or customer-supplied information, so that you can prepare high-quality, well-tested apps with a great UX.
If you have any questions, don’t hesitate to contact us!