Identity fraud recognition remains one of the major challenges for companies worldwide, as 69% of businesses surveyed by Regula claimed.
Improvements and advanced technologies used in identity verification solutions helps get to grips with the problem of identity document forgery. On the flip side, fraudsters adopt them as well.
Here are some current trends in identity document forgery that we, as a global developer of forensic devices and identity verification solutions, are seeing this year.
Subscribe to receive a bi-weekly blog digest from Regula
Which types of identity document forgery are in use?
Identity fraud has existed since the first ID documents appeared. There are dozens of tricks and techniques criminal entrepreneurs use. The basic ones are:
Manual alteration. This involves original documents issued by legal authorities and stolen from their original holders. Fraudsters change or erase some identification elements like a photo or name in the physical document. They can also add fake entry/exit stamps in passports with visas. Altered documents are also called forged.
Сounterfeiting. Some fake documents are made from scratch. To produce a compelling physical passport or ID, fraudsters can reach out to unscrupulous companies that produce security features, who will then provide them with access to authentic stamps, holograms, ink patches, and UV dull paper. They can also use empty obsolete blanks of documents as a canvas.
Computer simulation. Democratization of digital technologies has led to the rise of synthetic identity fraud (combining original data with fake). Another widespread technique involves selling empty ready-to-use blanks referring to a particular type of identity document. Also, there are digital services that allow one to make an ID card or driver's license from scratch. Since the process typically takes a couple of minutes and the result costs as low as $10 per item, many forgeries are produced this way. Unfortunately, such handcrafts might look compelling enough to deceive some identity verification systems.
Sometimes criminals mix these methods.
Why do fraudsters fake ID documents?
Countries with the highest level of welfare, such as the US, Canada, or Germany, come to mind first when speaking about the most often faked IDs and passports. Usually, they are destinations for illegal immigrants.
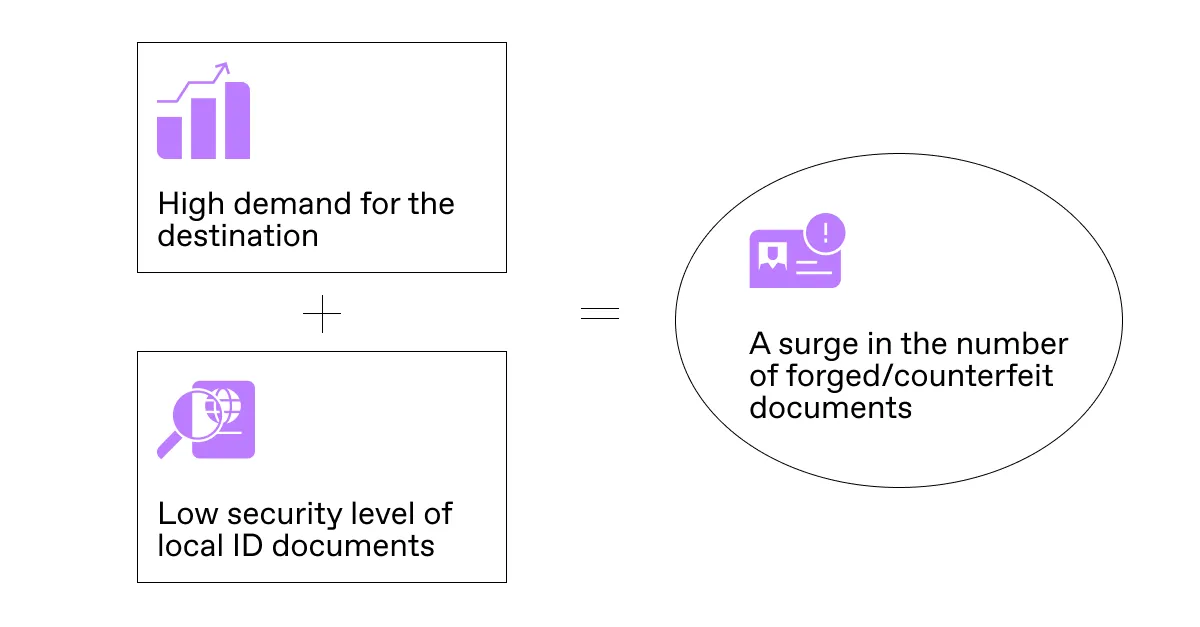
However, there are other factors influencing the identity counterfeit market.
Countries with weaker security measures used in passports and other documents usually have higher rates of forged IDs. The price of issuing legal identity documents indirectly reflects this. According to William Russel, an international insurer, an Australian passport is the most expensive travel document in the world now—$230 per issue.
The level of technological sophistication, including used security features, as well as the design complexity, affects the cost of the finished document. The more contractors involved in its creation, like designers, special paper suppliers, and printing services, the higher the cost is.
This also impacts what identity documents fraudsters prefer to use as a reference when making forgeries. As an example, getting an official Maltese passport costs $80; a Bulgarian passport is even cheaper—only $20. This partly indicates their low degree of protection in comparison to more expensive identity documents. As a result, both are now on the list of the most forged identity documents.


An Australian passport, which is more expensive than a Bulgarian one, boasts a greater number of security features.
High demand for a particular type of document matters as well. Today, Qatar and the UAE are examples of countries with a strong need for construction workers. This attracts many migrants from less prosperous regions, like India, Nepal, and Bangladesh. These workers can usually obtain short-term work visas, which allow them only 3 to 6 months of legal stay. As a result, there is a surge in forged passports and visas related to these territories.
Among the most commonly forged documents, traditional physical passports remain a prime target for fraudsters. Despite advanced security features, altering paper-based passport pages is still feasible for skilled forgers. Many countries with high levels of immigration, such as the UK, France, and Canada, continue to rely on physical passports as primary identity documents. Given the volume of international transactions and immigration, document authentication in Canada is crucial, helping individuals and businesses verify the legitimacy of official papers.
However, this doesn’t mean that other types of documents are completely protected from identity fraud. Regula’s forensic experts have come across cases when fraudsters changed photos on the personal pages of Finnish, Swedish, and Norwegian passports made from polycarbonate.
Since forged identity documents are primarily used as a one-way ticket to a new country, fraudsters sometimes create not one item but a full pack, including a passport, ID card, and driver’s license of the destination country.
Which sectors are most targeted by identity fraud with fake documents?
Primary hot spots include country borders, land checkpoints, and customs at airports.
Finance-related industries like Banking, Fintech, and Insurance also have to deal with identity fraud, since scammers try to access financial assets of all sorts. Although identity verification is mandatory for them, the level of security in business is not comparable to that at international borders.
Border control officers get regular training on detecting subtle signs of falsification in identity documents. It takes months and covers all security components and ways to examine them. Additionally, these specialists deal daily with broader document types when checking travelers entering or leaving a country.
Managers in banks or telecommunication centers have no such valuable experience. Typically, they deal with domestic identity documents. That's why a Thai passport might cause significant problems at a local bank office somewhere in Switzerland.
On the other hand, employees in commercial sectors are more likely to encounter homemade bogus documents than detailed document forgeries made by criminal pros, especially in remote customer onboarding and/or authentication scenarios.
Other industries like Healthcare or Education may mistakenly consider the identity fraud problem to be irrelevant to them. They are not bound by KYC compliance controls, which means they are also less aware of the identity fraud problem. Being less protected, these sectors often become an easy target for scammers.
How can businesses protect themselves from identity document forgery?
The bad news is that, one day, a fake or counterfeit ID card, passport, or driver’s license might be in your customer verification flow.
The good news is you can keep your systems secured and fraud-free by following these practices:
Put authenticity first
When creating forgeries, fraudsters focus more on visual similarity with original identity documents. But they often leave out essential details that are undetectable to the naked eye. This is where identity verification solutions come into play.
For instance, forged biometric documents mostly fail RFID chip verification. Scammers alter data in the visual parts of the document, such as the photo or name. However, they often forget (or just can’t) do the same in the other zones, like in the RFID chip. Advanced forgeries involve using cloned chips, but this can be detected using server-side chip verification.
The RFID chip is the most difficult to forge security component, so it should be one of the first to check. You can find more details on RFID verification in this blog post.
If you have a reliable tool, you can recognize inconsistencies in the visual inspection zone (VIZ), tiny alterations in the machine-readable zone (MRZ), and lack of security features, like photos or lenticular images. That’s what document readers do. Plus, many authenticity checks are available for digital onboarding scenarios involving identity verification as well.
Read also: How to Verify a Passport Like a Pro
Use a complete identity verification solution to check the input
As more identity verification sessions are done online, you need to avoid loopholes in your systems that attackers can exploit.
A well-architected identity verification solution usually has a server-side part where all checks are conducted in addition to the checks done on a smartphone. One component pulls data from users, such as a customer's ID scan or selfie, and sends it to the company's server, where a second component performs a set of authentication checks.
This approach guarantees that you will examine the very information the users provide you with in real time, not a third-party data pack dropped by fraudsters. That’s why SDKs can be a more secure option than APIs.
Rely on liveness checks
Equipped with a slew of complex security features, biometric identity documents are least likely to be faked, which explains their growing prevalence.
Although biometric fraud is often unsophisticated, you should still be on guard. Fraudsters come up with tricks that work in unsecured remote sessions. Luckily, many attacks with fake printed photos, video replays/injections, and 3D masks, are detected during liveness checks. This enables you to verify the realness of an image, whether it is a portrait or a scan of a passport.
Let’s have a look at Regula Document Reader SDK to see how this process might work in the real world. While checking the document's liveness, the software verifies the presence of dynamic security features, and performs a screenshot/electronic display check. Also, it matches the photo in the document with a selfie to ensure only real people access your service using a genuine physical document. This is also true for multi-factor authentication, including biometric factors like facial recognition.
Examine IP addresses
In remote scenarios, you can track a customer's IP address as they transmit their data to your systems. Further, you can create a blacklist of suspicious IPs to stop sessions and block traffic from them in the future.
For example, a session involving a client with a South African or Indonesian IP claiming to be a resident of Brazil should be red-flagged. Additionally, it’s worth paying attention to repeated attempts to get into your system from the same location. You also need to keep a watchful eye on situations when you receive repeated data from different geographies.
Have an extensive database at hand
Governments regularly update identity documents to cope with growing fraud. As a result, to reveal any fraudulent alterations, you need recent document specimens as a reference.
This means that any reliable identity verification tool must keep several versions of each ID and passport in its database. Then, you will be notified when a customer presents an obsolete document that has already been taken out of circulation.
An extensive document template database is also a protection against false positives. Since we live in an era of digital nomads, one day you may have to verify a driver’s license or passport issued outside your country.
How large should the database be? It depends on the scenario. The most comprehensive in the world is the one we maintain at Regula: it includes over 13,000 templates, and can cover almost any use case.
In conclusion
With the constant advancement of technology, fraudsters have become more sophisticated at forging identity documents.
While governments and law enforcement agencies continue to improve the security features on these documents to make them more difficult to forge, businesses should be vigilant and take necessary measures to prevent identity theft and fraud. This includes verifying the authenticity of identity documents before accepting them as valid. Regula solutions can serve as a good starting point.