With digital winning more and more spheres of our lives, it’s becoming vital to verify identity online to prevent fraud and personal data misuse. Identity verification is a method to ensure that a person—be it a user, customer, or client—is real and legitimate. Let’s figure out how identity verification works and how businesses from various fields can benefit from it.
We’ll deliver hand-picked content from Regula’s experts into your inbox
What is identity verification?
The chances are you’ve gone through identity verification many times in your life: in banks, while applying for social benefits, requesting insurance, or passing border control. In general, validation or verification of identity is the process of confirming that the personal information provided by an individual is authentic, valid, and belongs to them. The goal is to prevent all sorts of fraud related to the misuse of fake or stolen personal data.
Digital identity verification brings the same process online using remote document verification and biometrics verification technologies. Formally, the process can be divided into three parts:
Capturing and analyzing the data from an ID document to ensure it’s genuine and valid.
Capturing biometrics and conducting a liveness check to ensure it’s a real person accessing your service.
Matching a selfie with document data to make sure it’s not an imposter.
When identity verification is completed, the person is authorized to use the services they applied for.
We've collected everything on identity verification in one place. Explore Identity Verification from A to Z →
Identity verification vs. identity authentication: What’s the difference?
Identity verification and authentication usually go hand in hand, but some differences exist.
Verification helps to establish an identity online: to ensure the person exists and that their details are genuine, valid, and up to date. An integral part of the process is an identity document check. Some services ask users to upload scanned ID documents, a passport, or a driver’s license; others may require users to take photos with documents in their hands.
The term authentication can be used in two meanings which sometimes causes confusion.
First, authentication can often be a synonym for authorization or log-in—matching a returning user to their previously verified identity to let them in. In this case, it can include multi-factor authentication using email or phone. Sometimes there’s only a biometric check. An illustrative example of this is Apple Face ID, which allows you to unlock your smartphone and authenticate purchases by simply looking into the camera.
Second, authentication can also refer to in-depth identity verification, using data from a variety of sources, including investigative measures. One of the simplest authentication methods is security questions or a “shared secret,” such as the mother’s maiden name. More advanced methods include biometrics, such as face, fingerprints, or voice recognition. Regardless of the approach, the main idea here is not to rely on a single check, say biometrics alone, but to compare the data from multiple sources.
Steps of identity verification
As we mentioned earlier, there are three prerequisites for successful identity document verification: making sure an ID document is alright, capturing biometric data and conducting liveness tests to ensure it’s a real person, and matching the document with the biometrics to confirm they belong to the same person.
Identity verification protocols may vary depending on the technologies used or the industry's needs. Still, the basic steps will likely be the same in every case.
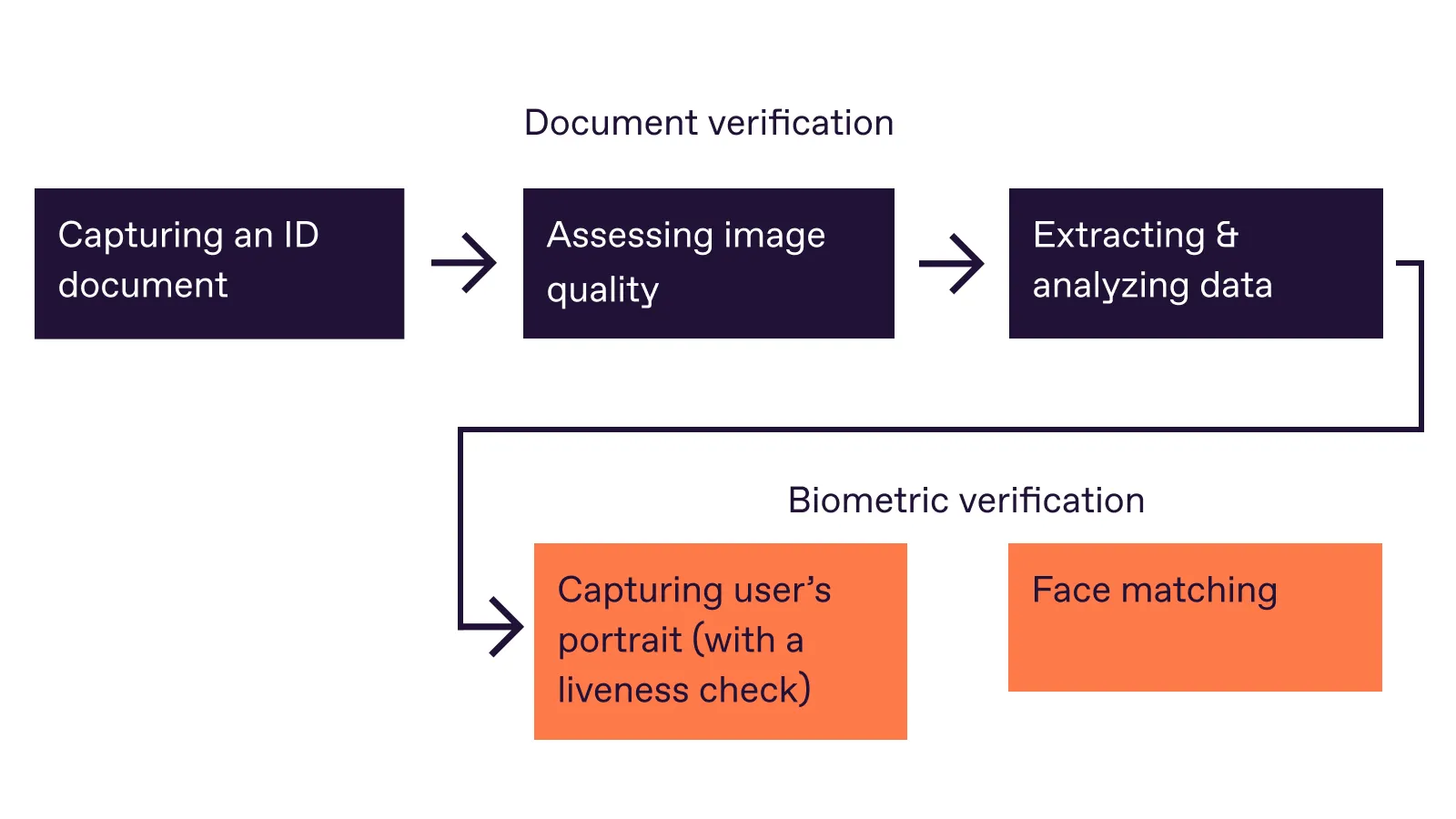
Step 1: Capturing an ID document

At the beginning of identity verification, users are asked to take a picture of their identity document. In most cases, people use physical ID cards, passports, or driver’s licenses, so it’s essential to capture them correctly. There should be no glares, and all important elements of the document must be clearly visible in the photo: if something is cropped or blurred, identity verification may be impossible.
Step 2: Assessing document image quality

Once the document image is captured, its quality is assessed and fine-tuned. For instance, if the brightness or contrast is not enough, the technologies can adjust it automatically to make sure the document is easy to read. Or, if the image is shot at an angle, the algorithm will help deskew it without affecting the readability of the data.
Algorithms also check document liveness to prove that the user captured a real document and didn’t falsify it in any way.
Step 3: Extracting and analyzing document data

ID documents around the world are different, but most of them have some elements in common:
A visual inspection zone
MRZ, or machine-readable zone
Barcodes
An RFID chip
Other security features
These elements contain ID holders’ data, which is represented or encoded in different ways. During the identity verification procedure, these elements are read, decoded if necessary, and compared with each other. If there are any contradictions, it might be a forgery. For example, it’s a relatively easy task for a counterfeiter to alter the data in a visual inspection zone, while replacing the data on an RFID chip is a much more serious challenge. That’s why they often damage the chip in an attempt to avoid being caught.
Document analysis starts with reading standard document elements, such as the MRZ, and identifying a portrait. The document holder’s image is fetched for further face comparison.
Advanced solutions, like Regula, are equipped with data parsing technology, and can automatically recognize the document type and country of origin, analyze the layout, and define what features (fonts, spacing, etc.) the genuine document must have. To be able to do this, the solution needs to have access to a comprehensive library of document templates. Regula’s database, for example, includes over 12,000 document templates from around the world.
Once the document type is defined, computer vision-based technology reads the visual zone, extracts textual and numerical data, such as a holder’s name, date of birth, etc., and fetches the data from present security features, e.g., barcodes. After it’s done, there are cross-checks to ensure all the data from different elements matches.
Step 4: Capturing the user’s live portrait

At this point, the user is required to provide biometric data. It might be face biometrics, fingerprints, or iris scans. The latter is usually required by state services (e.g. for visas), while businesses can only work with face biometrics checks. That’s why one of the most common ways to verify a user in digital services is by capturing a selfie.
It’s also essential to make sure the selfie is real. Liveness detection technologies help you check if the selfie was taken normally, without using masks, pre-recorded videos, GIFs, altered photos, or even deepfakes.
Step 5: Face matching

Once there’s a verified selfie, it is matched to all the holder's photographs in the document (including the one encoded on the chip). Face matching technology analyzes biometric data of each face image and compares them. If there’s a match, the verification is done.
Additional steps
Once the documents and the user’s identity are verified, there might be additional steps depending on the industry. The user can be additionally checked against various databases and watchlists, such as AML, PEP, etc. In any case, flexible identity verification solutions allow you to tailor the process to your business needs.
What industries need identity verification services?
Taking into account the ongoing digital transformation trend, almost any industry can make use of user identity verification. For some businesses, however, it’s already a must. Among them, there are:
Banking and financial organizations
Government-related services
Aviation companies
Cryptocurrency-related services
Insurance and medical help institutions
Hotels, casinos, and entertainment companies
Car, scooter, or bike-sharing services
Digital identity verification brings these industries automated remote registration and onboarding, along with better risk management, compliance, and increased customer trust.
Why is an identity check a must for so many industries?
There are two reasons for this: protecting businesses and protecting consumers. Thanks to identity verification, businesses shield themselves from various service misuse cases, comply with the law, and minimize risks of fraud or cybercrimes.
Although IDV procedures often add extra friction for end customers, it also works in their best interests by keeping fraudsters willing to misuse other people’s data at bay, as well as protecting minors from age-restricted content or goods. Verification can be also seen as a flipside of online customer onboarding that allows convenience and personalized service.
Reduced fraud & cybercrime risk
Fraudsters often pretend to be legitimate customers to access services and use them for criminal purposes, such as money laundering. Identity checks help to be one step ahead of such deception.
For instance, financial institutions do their best to recognize and prevent fraud whenever someone’s opens a new account or tries to access an existing one. If the customer is new, identity document verification and real-time facial comparison can prove that the user is not trying to open an account on behalf of someone else. And if the user already has an account, face recognition or biometrics prove that it’s the actual owner trying to access it. This keeps money and data safe and helps build trusting relationships with customers.
Increased compliance
In many countries, organizations from specific fields must comply with anti-money laundering (AML) and Know Your Customer (KYC) regulations. This means they have to gather a sufficient amount of personal information about each customer, run identity checks, and monitor whether their services are used for legitimate purposes.
Failing to comply can lead to civil and criminal penalties, from fines to jail sentences, let alone reputational damage. A reliable solution for verifying identities can insure businesses against these risks.
Enhanced trust between users and businesses
Identity verification increases transparency and trust in relationships between users and businesses. Compliant businesses which are comfortable with AML & KYC policies appear reliable for potential customers while being able to suggest more tools to the customers based on their data, and, as a result, gain a competitive advantage.
The same two-sided process works for users on P2P platforms and marketplaces. If you have verified your identity and all the other users have done the same, you can feel confident that you’re dealing with real people.
Improved customer onboarding process
Online has become an important channel for attracting and interacting with customers who have gotten used to getting almost every service remotely. Digital identity verification solutions can make it happen with little to no friction, while also keeping the business and customers safe.
Automated identity verification reduces the time required for manual checks, accelerates data entry, and makes processing it much more accurate. This can significantly speed up airplane onboarding, hotel check-in, or account creation. As a result, onboarding becomes quicker, requires less effort from both sides, and errors become rare.
The future of identity verification services
Winning customer trust and providing the best user experience are vital for success these days. With more and more life spheres turning digital, the demand for reliable and scalable identity verification solutions will keep growing. These technologies are evolving fast, embracing artificial intelligence and big data to recognize and prevent fraud, fakes, and manipulations. At the same time, we’re likely to face increased fraud attempts and stricter regulations.
Hopefully, these trends will shape a transparent digital future where all data is safe and well-managed, and our routine tasks are quick and easy, leaving us free to be wherever we want with the same access to services.





