In an age of digital passports and mobile driver’s licenses, the term “digital identity” has gained a broader definition. Historically one of the components of an information system, it can now be a critical asset for digital businesses—and must be highly secure.
This article outlines the evolution of digital identity over the decades to reveal its current applications, shed light on related threats, and explore its future.
What is digital identity?
At a basic level, a digital identity is a unit in a digital environment representing a particular component—a human, device, software program, endpoint, or even an organization. It’s a set of measurable characteristics that can help identify different entities within the system.
For example, one computer can identify another through an IP address. To identify a person, their email and password combination can be used.

However, a digital identity isn’t the same as a user, which is a more complex entity with a particular place in the system’s access hierarchy. The higher the user’s access level, the more system resources and features are available to them.
For instance, take a marketplace: compare an admin who manages all components in the system to a regular user with a limited set of operations like logging in, checking out, and editing a profile.
Additionally, non-human identities like computers and servers can also be users with a digital identity.
From here on, we’ll focus exclusively on digital identities related to humans.
Subscribe to receive a bi-weekly blog digest from Regula
How to distinguish different digital identities
For proper handling, a system’s digital identities—with their identifying characteristics or identifiers—are stored in its identity and access management (IAM) system. This establishes access controls through user authentication (confirming identity) and authorization (defining access level).
There are at least three types of identifiers:
Inherent—Something an individual possesses always (biometrics like facial scan, fingerprint, or iris scan)
Assigned—Something an individual gets from a third party (e.g., Social Security Number, passport number, or mobile number), or creates in the system as their identifier (a username, email address, or password)
Accumulated—Something that describes the user’s activity in the system (general behavior under the account, like purchase or search history, IP addresses used for logging in, profile edits, etc.)
These characteristics can be used alone or in combination, determining the particular checks used for digital identity verification.
For instance, in a very simple scenario, an individual enters their username and password to log in to the system. If this username/password pair matches the one stored in the IAM system, the user is authenticated and can use the service according to their authorization level.
In many services, email addresses or mobile numbers can be used as usernames.
However, password verification is now the least secure option. This can be strengthened by additional controls—such as email verification or a one-time password sent to the user’s mobile number.
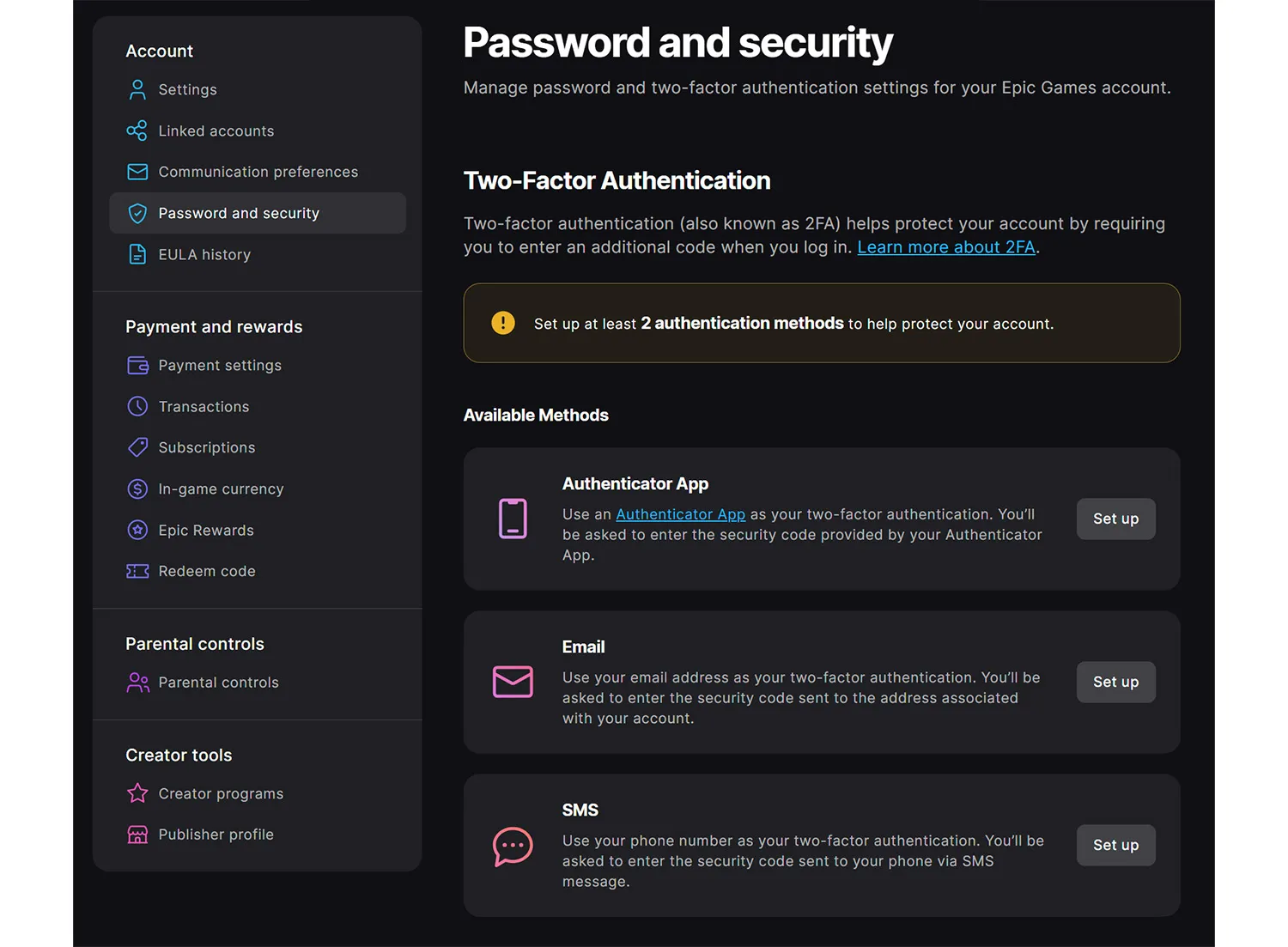
Many companies like Epic Games offer two-factor authentication as a security measure, letting users choose which additional identifiers work best for them.
More advanced authentication methods include biometric components like facial scans. In such cases, biometric verification is required. This check typically involves face matching with liveness detection to confirm that the user is both legitimate and real.
Three application levels of digital identities
According to Statista, there are 5.56 billion internet users worldwide. Since one user typically has several accounts, there are zillions of digital identities.
For better understanding, this variety can be represented in a three-tier model:
Personal level: Digital identities that people create voluntarily—for instance, on social media platforms or in dating apps—for communication needs. These identities can be closely matched to real individuals, containing their authentic photos and names, or fully anonymized.
Commercial level: Digital identities that people create to access particular services, such as mobile banking, ecommerce shopping, or mobility services. In this case, the need for an identity is set by businesses. Commercial digital identities often rely on stronger identifiers, such as card details or residence addresses.
Governmental level: Digital identities that people are required to create to access governmental services like applying for allowances or managing taxes. Registration in such systems usually requires a full set of personal information, meaning deanonymization.

Across different levels, there is often an inverse correlation between defense and anonymity.
Personal digital identities
At this level, users tend to create digital representations of themselves on the web. There are two opposite approaches: some prefer to act anonymously, hiding their identities under fake names and avatars, while others are ready to show their real personality. In the latter case, people often upload sensitive information—such as photos or personal details, including addresses and phone numbers.
Unfortunately, when creating online personal accounts, many users still rely on unsafe identifiers and weak access controls, using easy-to-break passwords and single-factor authentication. As a result, mass data breaches regularly hit this part of the internet. Over 16 billion login credentials, passwords, and emails associated with platforms like Google, Facebook, and Telegram have recently been exposed—and that’s just one example.
Commercial digital identities
At this level, businesses—banks, telecoms, crypto exchanges, etc.—set the rules. This may add extra safeguards to customers’ digital identities, as companies often follow strict regulations such as Know Your Customer (KYC) and Anti-Money Laundering (AML) requirements.
For example, signing up for a mobile banking app requires not only a login/password combination but also confirmation of identity through government-issued documents and selfie verification. In addition to personal details that a bank collects, like full name, date of birth, and address, it also monitors customer activity—i.e., it uses accumulated identifiers as an extra security measure.
With all these safeguards, you might think that commercial digital identities are invulnerable. Yes, they are usually better protected than personal accounts, but the defense level still highly depends on the industry and region where a company operates. Not all businesses are regulated by KYC/AML frameworks. What’s more, these regulations may differ from country to country. For example, compare the rules in the UAE, where a single digital KYC platform for local companies is now being developed, and in Türkiye, where different sectors still have to comply with specific requirements independently.
What are verifiable credentials and reusable identities?
These options can also be considered digital identities; however, they have specific characteristics that distinguish them from ordinary identifiers.
Verifiable credentials are personal details about an individual (“is over 18,” “has a driver’s license,” “works at Y”) that are signed cryptographically. They enable users to confirm their identity, age, or employee status across different digital services. Individuals have full ownership of their verifiable credentials—typically stored in a digital wallet—and decide what data to disclose.
A similar concept and architecture lies at the foundation of reusable identities. However, this form of digital identity is more of a wallet-based identity profile than a set of granular attributes. Once created and verified, a reusable identity can be used online as proof of identity.
Governmental digital identities
These are digital identities operated by government agencies. Typically, they are fully deanonymized and linked to entries in governmental databases containing personal data from identity documents, and often biometric data as well. Interestingly, these identities can sometimes be created on-site, when an individual visits an official registry office in person to provide their ID and submit fingerprints or a photo. However, online registration scenarios also exist.
The primary purpose of this type of identity is to provide online access to community and social services, tax payments, business registration, etc. In most countries, there are special mobile apps or all-in-one web platforms that support this use.
Despite higher security requirements at this level, the security of governmental identities varies. For instance, users of Australia’s myID can choose between three identity strength tiers. For comparison: the basic account requires only personal details and at least one verified ID document, while the strong level requires a passport, an additional proof of identity such as a driver’s license, and a face verification check. The higher the tier is, the more services are available.
The latest step in the evolution of governmental digital identities is full-fledged digital IDs that replace physical documents during both remote and on-site verification.
Key threats for digital identities
Regardless of who creates a digital identity or where, it remains vulnerable at all application levels. However, the degree of vulnerability depends on defenses and infrastructure, including the current IAM framework and the identity fraud prevention and detection strategies in place.
Generally, there are at least three potential issues associated with digital identities:
All kinds of identity fraud
In its initial form, a digital identity often has a high level of anonymity and is based on depersonalized identifiers like passwords or email addresses. This makes it a perfect tool in fraudsters’ hands, especially at a personal level. They use fake identities in a variety of ways—for example, to send phishing emails aimed at account takeovers.
Advanced tech like deepfakes and other AI-generated tools have recently been added to the criminal toolkit, offering more opportunities to create fake personas and identity documents and bypass business defenses. Scammers can impersonate legitimate users, take out loans using synthetic identities, use deceptive financial techniques like smurfing, commit healthcare insurance fraud, and much more.
For individuals, this often leads to data breaches and financial loss, which always impact a platform’s reputation negatively. For businesses, identity fraud may additionally result in penalties and fines from regulators. Government risks are the highest, since national identity systems store the personal data—sometimes including biometrics—of all citizens and residents. Any disclosure or compromise puts national security at risk.
Lack of digital hygiene
From employees to Instagram users, people tend to ignore security recommendations when it comes to their digital identities. Weak passwords, reusing the same credentials across platforms, and skipping multi-factor authentication remain common behaviors.
Also, not everyone knows what to do if their account is compromised—at all levels.
Businesses and government agencies try to address this problem by running educational campaigns and offering checklists for victims of identity fraud and data breaches. However, mandatory security measures—like super strong passwords and biometric authentication—are likely to be more effective than awareness campaigns alone.
Technical hurdles and privacy risks
Finally, with the emergence of new forms of digital identities—from verifiable credentials to digital IDs—global interoperability has become an issue. While businesses and governments are transforming their identity systems, it’s still critical to keep these systems part of a connected, global ecosystem.
This challenge is highly sensitive, as next-gen digital identities require establishing trust between all parties involved. In today’s world, that trust is not easy to earn. In addition, upgraded infrastructure is needed to connect identity holders, issuers, and verifiers across borders.
In practice, industry players show very different approaches—both domestically and regionally.
For instance, in China’s recently launched framework, real and digital identities are tightly linked. After verifying their identity using physical documents on an official platform, users receive a unique internet ID number and a digital certificate that corresponds to their real-world identity. This number can then be used for authentication across the web.
While centralization appeals to governments, decentralization tends to appeal more to users. In the EU’s eIDAS framework—a more user-centric approach—people use digital identity wallets to access public and private services. These wallets are controlled by the users themselves and function similarly to reusable identities. Currently, eIDAS-compatible wallets are still under development in many EU countries, and broader use is expected by 2026.
The next chapter of digital identity
Starting as a unit in the global network, digital identities continue to evolve. In practice, they form diverse ecosystems that operate independently within a company or state.
In an ideal world, these smart ecosystems would communicate with each other. But that might only be possible if there is no conflict between government systems, tech giants, KYC providers, and businesses. Trust is definitely the solid foundation for cooperation between all actors.
However, trust isn’t built by scale—it’s earned through accuracy and reliability.
Regula’s role in building a more secure digital identity future
As one of the key players in the identity verification field, Regula offers compliant solutions trusted by banks, border controls, fintechs, airlines, and other businesses worldwide:
Document Reader SDK—On-prem, fully customizable software for remote ID document verification that goes beyond standard authenticity checks, providing border-level accuracy.
Face SDK—A solution for facial recognition and face matching, enabling reliable biometric checks with liveness detection smoothly built into your flow.
Feel free to book a call to discuss your requirements and expectations!





