What’s on the list?
We've chunked the topics for the identity verification domain into six chapters. Click on the chapter you’re interested in to jump right there or scroll down for a list of all of our articles.

Chapter 1:
What Is Identity Verification?
Just like any other industry, the identity verification field is full of buzzwords. So before we go further, let’s make sure we’re on the same page and sort the main terms out.
What is identity verification?
At its core, identity verification is the process of confirming that a person is who they say they are. This process is commonplace across various scenarios, from government agencies to online services. The essence of identity verification lies in validating the authenticity and validity of an individual's personal information. The ultimate goal is to prevent fraudulent activities that involve the use of fake or stolen identities.
The digital world has adapted traditional verification methods to online platforms through technologies like remote document verification and biometrics. This process typically involves three critical steps:
Document analysis: Verifying the authenticity and validity of an ID document.
Biometrics and liveness checks: Ensuring that a real person is present and accessing the service.
Face matching: Confirming that the person is not an imposter by comparing their live photo with the one on their document.
This streamlined process not only secures transactions and interactions, but also provides a smoother user experience, granting access to services once verification is complete.
Identity verification vs. identity proofing and identity authentication
While often used interchangeably, identity verification, proofing, and authentication serve distinct purposes.
Identity proofing is often perceived as the formal groundwork of confirming someone's identity. The term is primarily embraced by official bodies and regulatory institutions.
Identity verification typically refers to the technical procedures used to validate an individual's identity claims. This involves practical steps like analyzing ID documents and biometric data to confirm that the person's details are genuine and valid.
Identity authentication can refer to two different things. First, the term can be used in the sense of confirming the identity of a returning user before granting access to services. Second, it can also mean in-depth identity verification using data from a variety of sources, including investigative measures.
The identity verification process in action
The identity verification process unfolds in meticulously designed steps to ensure thoroughness and accuracy. As we mentioned above, two terms—identity proofing and identity verification—are often used interchangeably. The infographics below illustrate the difference between these two related frameworks.
While the stages don’t match exactly, all the identity verification steps are used within the identity proofing process:
| Identity proofing steps | Identity verification steps |
|---|---|
1. Initiation | N/A |
2. Attribute & evidence collection | 1. Capturing an ID document |
3. Attribute & evidence verification | 3. Extracting and analyzing data |
4. Binding to the applicant | 4. Capturing the ID portrait and performing a liveness check |
Issuing the result | |
Learn more:
What Is Identity Verification & How Is It Done? An Explainer
What Is Identity Proofing & What Proofing Techniques Does It Imply?
How Companies Embrace Digital Identity Verification: Real Examples Analyzed

Chapter 2:
ID Document Authentication
Government-issued identity documents are the cornerstone of identity verification. Thus, the capability to assess the document’s authenticity with a high level of confidence is a must for any organization, from SMBs to enterprises.
Below, we delve into the crucial process of ID document authentication, and uncover some of the security elements that help us conclude if a document can be trusted—both offline and online.
What is document verification?
Document verification is a critical process, especially for sectors like Aviation, Banking, Fintech, and Gambling, where it's a legal necessity. The traditional manual checking of documents is thorough, but comes with challenges: it requires seasoned experts, takes time, and is prone to human error.
At the same time, users expect swift and secure access to services—even the most regulated ones—so efficiency and accuracy in document verification are more important than ever.
Automating document verification is a game-changer
Automated document verification relies on specific software and devices designed for this task. While it doesn't completely remove human involvement, it significantly reduces the workload by handling the bulk of the verification process. For example, automatic gates at airports can quickly check a traveler's ID. However, if any issues arise during this check, a staff member steps in to manually review the situation.

Automated document verification isn't just fast; it's also remarkably trustworthy. This reliability stems from several key factors:
Advanced technological foundation: Automated document verification is built on advanced technology, including optical character recognition (OCR), biometric analysis, and artificial intelligence (AI). These tools allow the system to closely examine document details that people might miss. This thorough analysis helps catch forgeries and any subtle alterations with great accuracy.
Continuous learning & improvement: Automated systems learn from each verification case, constantly expanding their knowledge base so that with every document scanned, the system becomes even more adept at spotting sophisticated fraud techniques. This ongoing learning process enhances the system's reliability over time.
Global standards: Automated verification systems are built to comply with international standards and best practices for document security. They are regularly updated to reflect changes in document designs, security features, and regulatory requirements worldwide. This ensures that the verification process is consistent and also up-to-date.
Cross-check capabilities: Beyond examining the physical and visual aspects of a document, automated systems can cross-verify information against databases and other digital resources. This added layer of verification further bolsters the reliability of the process, confirming the authenticity of documents against trusted sources.
Expertise at scale: Developers of automated document verification solutions, such as Regula, bring years of expertise in document forensics to their tools. This deep knowledge is built into the automation algorithms, guaranteeing high-quality document checks on a large scale.
The role of comprehensive databases of document samples
Effective document verification crucially depends on one key resource: a comprehensive database of ID document samples. This database serves as a benchmark for comparing submitted documents to verify their authenticity.
In a manual verification setting, it's unrealistic to expect an inspector, particularly those stationed at busy international checkpoints, to be familiar with every possible form of ID from around the world, along with their numerous variations.
In automated verification systems, the breadth and depth of the document database directly impact the system's capability to function effectively on an international scale. The ability to recognize and verify a wide range of documents from various countries is essential to operating in a global market. This requirement underscores the necessity for automated verification solutions to be equipped with a comprehensive database.
A well-maintained and expansive database is the backbone of any document verification system. Such a database isn’t a static collection but a dynamic resource that includes detailed specifications, security features, and updates reflecting the latest versions of ID documents. The robustness of this resource determines the solution's effectiveness in ensuring the integrity of the verification process.

Learn more:
What Is Lenticular Printing Technology and How It Secures Identity Documents
What Are Covert Laser Readable Images and How to Make Them Overt
Regula Identity Document Template Database vs. Information Reference System: What’s the Difference?
How Regula Creates the Most Full and Detailed Document Reference System


Stay Tuned!
We'll deliver hand-picked content from Regula's experts into your inbox
Chapter 3:
Scanning & Reading ID Documents
Reading a document seems easy, but it’s not. Even if you put aside their huge diversity, some personal data just can’t be interpreted if it’s extracted by ordinary OCR. Here we have some insider tips on how best to handle ID documents.
Tip #1: Employ advanced document parsing rather than mere OCR
While OCR can digitize text from images, making scanned ID documents editable, it often falls short when it comes to structuring and validating this data—critical steps for processing ID documents efficiently.
Advanced document parsing goes beyond OCR by organizing, analyzing, and verifying captured data. This approach leverages comprehensive document template databases. Such a database should contain a vast collection of software algorithms designed for the machine-based processing of a specific document. The more templates in the database, the more diverse IDs it can handle.
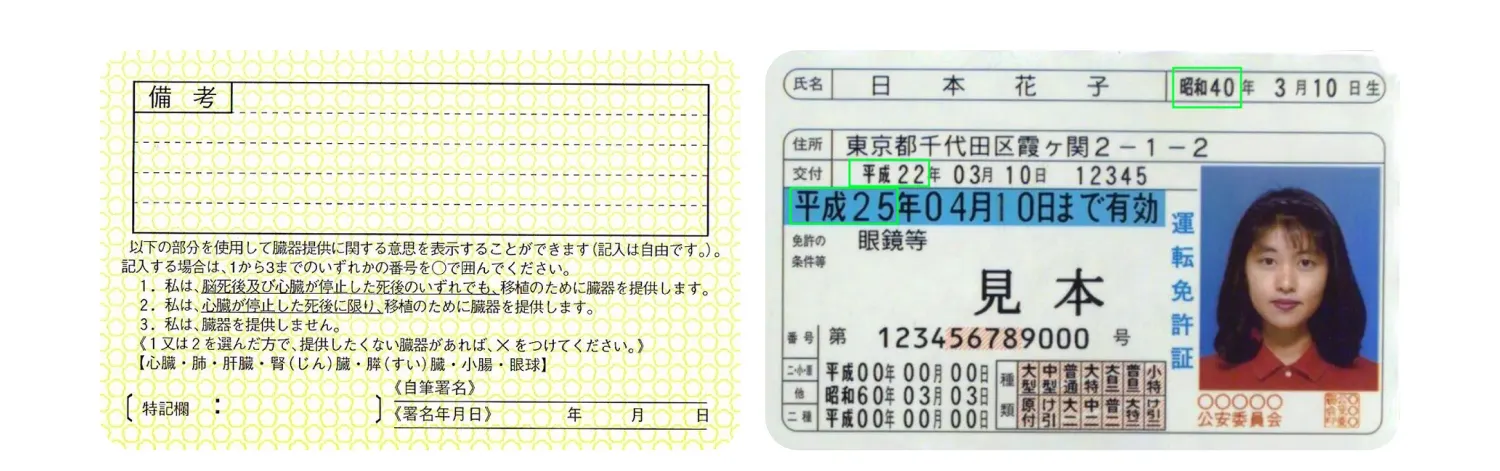
Japanese driver’s licenses may differ on the front side but have the same back layout. As a result, two driver's license types would have three templates.
💡When we say “diversity,” we really mean it. Here’s our series on the peculiarities of identity documents issued in different countries (and the list is growing!):
Here’s what makes document parsing a must-have for identity verification:
Automatic document type detection: Identifies documents, ensuring that each document is processed according to its specific requirements.
Data extraction & structuring: Accurately extracts relevant data fields (e.g., name, date of birth, document number, and user portraits) and organizes them so that they can be easily used and re-used.
Data validation: Employs complex algorithms to check (and cross-check) the extracted data against document-specific rules and databases for anomalies or inconsistencies. This reduces the risk of fraud and ensures compliance with regulatory standards.
Multi-language support: Interprets and processes documents in multiple languages, including non-Latin script, making it an invaluable tool for global operations.Tip #2: Don’t underestimate the importance of proper MRZ reading
The Machine Readable Zone (MRZ) is a critical component of many ID documents. It contains encoded data essential for authentication and verification processes performed by software-based tools.
Many IDV providers wave it off as something super easy, but we wouldn’t recommend falling under this false sense of simplicity.

An example of one of the most common MRZ types in a Finnish passport.
The system you choose has to be ready to handle a range of non-standard codes used in ID cards around the world. Otherwise, you may encounter a lot of false positives or even missed errors. Here are a few ideas on what to look for in a tool for optimal MRZ reading:
Advanced capture capabilities that can read the MRZ from any angle and detect it even in low-res images.
No less than 200 different parsers to handle all possible MRZ types, including non-standard ones.
Capabilities that verify whether all the data is appropriate, valid, and conforms to a specific MRZ type (e.g., confirming that a document’s code doesn't contain placeholders and/or inappropriate symbols).
Performing cross-checks to detect any mismatches between MRZ data and information in the visual inspection zone and an RFID chip, if applicable.
Examination of check digits.
Tip #2: Implement RFID chip checks to verify electronic documents
RFID (Radio Frequency Identification) is a technology that uses tiny electronic tags and readers to wirelessly transmit and receive data. In electronic identity documents, this "tag" takes the form of a microchip embedded within the document itself.

To verify RFID chips, specialized readers or NFC-enabled smartphones establish secure communication with the document's embedded chip. However, the increasing trend of verifying ID documents remotely, with NFC-capable mobile devices acting as readers, introduces potential security vulnerabilities that fraudsters could exploit. For example, a fraudster could use a genuine passport with an RFID chip containing cloned information from another document.
Addressing this security gap requires a "zero-trust to mobile" strategy, implemented through server-side RFID verification.
Once the user's device has completed the chip checks, it transmits the chip data and verification results to a secure server for further review. Should server-side verification uncover any inconsistencies or indicators of fraud (such as non-standard encryption techniques, signatures linked to invalid or fake certificates, etc.), this suggests that the chip's data or the chip itself may have been compromised during the initial verification process.
Learn more:
Data Parsing vs. OCR: What Is Better When It Comes to ID Reading Automation
RFID Technology for Identity Verification: A Comprehensive Guide
Why NFC Identity Verification Is the Best Thing for Regulated Industries

Chapter 4:
Biometric Verification
Biometric verification identifies and authenticates individuals using unique biological traits that remain consistent over time, such as facial features, fingerprints, and iris patterns. This method stands out for its accuracy in answering two fundamental questions:
"Who is this person?" — for identification;
and "Is this person who they claim to be?" — for authentication.
An essential step in the identity verification process is to bind an ID to its rightful owner. This is typically achieved by prompting users to take a selfie or record a short video of their face, which is then biometrically compared with the photo on the document and the one encoded in the chip.
Facial recognition is most popular in the commercial sector
Facial recognition technology has emerged as a favored method for businesses due to its accuracy, remote and contactless verification capabilities, and adaptability across various platforms.
The technology finds extensive application in industries such as Aviation and Transportation. Some examples include self-check-in kiosks at airports and mobile apps with face recognition modules, like those provided by WizzAir and airasia, streamline passenger processing.
Major banks, including UBS, leverage facial recognition for customer onboarding, offering a fast, frictionless, and secure verification process. The technology is also essential in the Cryptocurrency and Gambling sectors, primarily to verify users’ age and validate transactions.
How facial verification technology works
Facial verification technology operates through two main approaches: active and passive authentication.
Active Authentication: Requires users to perform specific actions, like head movements, to confirm their liveness.
Passive Authentication: Requires only a user selfie. Advanced algorithms assess liveness and authenticity in the background.

Historically, active authentication emerged earlier. The evolution from active to passive authentication reflects improvements in mobile camera technology. At that time, it was challenging for most users to shoot a high-quality selfie that would work for a credible liveness check.
As taking high-quality selfies becomes more accessible, passive authentication for liveness checks has gained wider adoption. Snapping a photo is much faster and more user-friendly than making users repeat randomly generated actions.
However, the success of passive authentication hinges on the quality of the selfie. Blurry photos can obscure essential facial features, so it’s key for identity verification solutions to include robust image quality assessment capabilities. Advanced image capture modules that optimize glares, shadows, head position, and face size are crucial for minimizing the need for retakes and enhancing the user experience.
Learn more:
Biometric Verification Unveiled: Understanding the Basics and Benefits
Passive Authentication With Liveness Detection: What Is It & How Does It Work?
What Is an Age Verification System and Why Incorporate It Into Your Business
What Is Liveness Detection, and How Does It Help to Address Online Authentication Challenges?
How to Employ a Face Recognition Process in Identity Verification and Why

Chapter 5:
Identity Fraud
There have always been fraudsters who pretend to be someone else to get illicit benefits and avoid being caught. The accessibility of technologies and the trend toward everything remote have only made this worse. However, fraud prevention technologies have been evolving too.
Here, we outline the primary threats to identity verification, and propose measures to counteract them.
→ Fraudsters attempt to use fake, stolen, or revoked IDs
First things first: non-electronic ID documents, lacking embedded security features like RFID chips, pose a significant risk for remote verification. That’s why it’s important to prioritize electronic documents with embedded chips for verification. For documents without chips, it’s better to request additional evidence to bolster the verification process.
Also, the rule of thumb during remote verification is utilizing video capture for document presentation to more effectively examine security features and detect irregularities.
As for fraudsters using stolen or revoked documents to impersonate others, an effective countermeasure is implementing biometric checks to compare the presenter's face with the document photo. The ideal solution is to accept electronic documents only so you can use chip data for comparison and re-verify the data on the server side to fully ensure its integrity.

This technique is called face morphing. If a fraudster succeeds in getting a morphed image in an ID, two or more people can potentially share it.
→ Fraudsters submit rare document types, hoping inspectors will fail to scrutinize them
The vast array of global ID documents presents a challenge in ensuring comprehensive verification support. Even the most skilled inspector can face an unfamiliar document which they need to somehow verify. The only solution here is to ensure your system supports a wide range of document types, and is regularly updated to include new documents and variations.
Another tip here would be to automate the verification process as much as possible. Robust technology reduces human error and tremendously increases the speed of operation, while a hybrid approach combines human expertise with machine learning for added security.
→ Fraudsters manipulate the quality of ID scans
Sometimes fraudsters deliberately capture documents in such a way as to make them look worse. For example, they may tweak the image quality or just capture a photo in poor lighting conditions. As a result, some critical document features can’t be properly verified.
To prevent this, you need to establish quality standards for document submissions, rejecting those that do not meet these criteria.

→ Fraudsters use images or videos instead of real documents
In an attempt to fool automatic systems, fraudsters might put a screen in front of the camera instead of a genuine ID.
To avoid this, you need to implement a document liveness feature. It ensures the document is physically present during a remote session by performing a screenshot check and verifying the presence of dynamic security features, such as holograms and moire effect.
→ Fraudsters try to manipulate captured data
Fraudsters alter or intercept data during the identity verification process, manipulating the information before it's transmitted to the verifying party. This can include altering the data on the user's device or intercepting the data in transit, potentially resubmitting altered or stolen information.
To combat this sophisticated form of fraud, it's crucial to:
Never trust verification results obtained from users’ mobile devices. Instead, conduct server-side verification to double-check all data received.
Implement end-to-end encryption for all data transmission, ensuring that data intercepted in transit remains inaccessible to unauthorized parties.
Securely store data on your server within a secured perimeter, so that you can always double-check the results in the future. To stay safe, an identity verification vendor ideally should offer on-premises options.
→ Fraudsters can present a photo or a video recording instead of a live person, or wear a mask
In an attempt to deceive identity verification systems, fraudsters may present a photo or video recording of another person instead of appearing live. They can also attempt to use masks, from cut-out photos to highly realistic silicone masks, to impersonate other people.
This challenge is effectively mitigated by liveness check capabilities, which are pivotal in ensuring that the verification process involves a real-time, authentic representation of the applicant.
Learn more:
Identity Fraud Statistics: How Businesses Respond to the Issue
What Is Identity Theft: Definition, Common Types, and Prevention
A Guide to Synthetic Identity Fraud: Definition, Targets, and Precautions
Facial Morphing: Why It Can Threaten National Security & How to Protect Against It
Identity Fraud Detection and Prevention: Insights from the CTO's Desk
The Impact of Deepfake Fraud: Risks, Solutions, and Global Trends

Chapter 6:
Identity Verification Toolkit
While we definitely wouldn’t want to downplay the skills of human expert inspectors, the fact is that effective identity verification today heavily relies on automated tools. Here we shed light on how it works behind the scenes.
Hardware solutions: Document readers
Document readers, often referred to as ID scanners or passport readers, are integral to an identity verification toolkit. Their capabilities extend beyond mere data entry automation, offering features such as document authentication and examination of security features under various light sources.
The hardware segment includes:
Desktop Document Readers: Compact, affordable, and widely used for advanced authenticity checks in banks, immigration services, and border controls.
Embedded Document Readers: Core components of self-service registrations, kiosks, and e-gates, offering durability and advanced verification capabilities.
Mobile Document Readers: Portable and versatile, ideal for use by law enforcement and border patrols for on-the-spot data processing and analysis.

Software solutions for identity verification
Software solutions, often deployed as Software Development Kits (SDKs), enable reliable customer onboarding and verification in remote scenarios. Their key features include document type recognition, data validation and verification, and biometric checks.
Such solutions leverage the power of users’ devices, but we will never tire of repeating that, for reliable results, it is necessary to cross-check the obtained data inside your own secure perimeter.
Learn more:
ID Scanners: How They Work, Types, and Choosing the Right One
ID Document Reader Buyer’s Guide: Choosing a Future-Proof Device for Automated ID Verification
Neural Networks in Identity Verification: How AI Streamlines the Process
9-Step Guide to Choosing the Best Identity Verification Software
Cloud vs. On-Premises Identity Verification: Which Approach Is Right for You?
Identity Verification Metrics: How They’re Calculated and Why They Often Mislead
Identity Verification Solution Pricing Models: Choosing What Fits You Best